First Time Installation (SSO)
Installation Requirements
These instructions will guide you through a complete standard XA Server setup using Windows Authentication mode. Please consult your HealthCast Project Manager if you are interested in an alternative method.
These instructions are also valuable tools in troubleshooting possible XA Server issues. For troubleshooting, use this document to ensure that the two XA Servers have been correctly configured. The source of a problem may be quickly identified by reviewing the high-level steps to confirm that they have been properly followed.
Warning
DO ALL STEPS IN THE ORDER IN WHICH THEY APPEAR. In this configuration, XA and Microsoft SQL will be installed in the same server. For ease of use, this document reflects only the instructions for this standard configuration. Start with a clean server or server image to ensure all software is optimally configured.
Load Balance the two XA Servers.
Install XA Server.
Configure failover for each server service.
Configure replication for each server database.
Test the entire setup to ensure it is functioning as intended.
Ensure that your environment meets the Target System Requirements
Log in to the server, on which you will install XA Server, as an administrator with permissions to write/read/modify system folders.
Locate the installation files provided by HealthCast and have them saved in an accessible location.
Active Directory
Necessary Active Directory Accounts
An AD group named XA ADMINS.This is a global security group for administrators of XA.
An AD user named xaadmin.This user account should be a member of the XA Admins group and be set so that the user cannot change the password and the account never expires.
An AD user named xaserver. This user account should be a member of the local Administrators group on each server in which XA is installed. It should also be set so that the user cannot change the password and the account never expires.
Create a group
Login to your network Domain Controller.
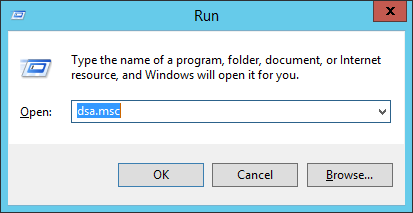
Open Active Directory Users and Computers (ADUC).
This can be done quickly by selecting Start > Run and entering dsa.msc (the ADUC MMC snap-in) into the Run dialog box.
Create a new security group named XA Admins in the domain.
Select the global and security options during the group setup process.
Users in this group will have privileges to administer XA.
Users in this group do not need domain administrator privileges.
Create an ExactAccess Administrator account
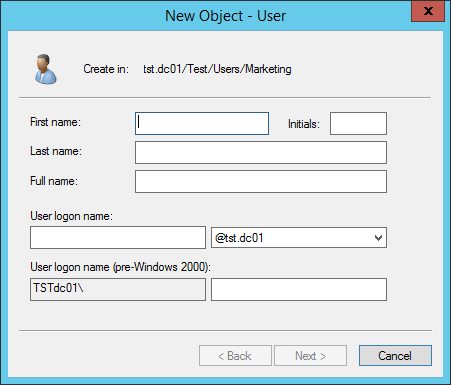
Create a new domain user named xaadmin.
Select the appropriate boxes during the set-up to set the password so that the user cannot change it and it can not be expired.
Add xaadmin to the newly created XA ADMINS global security group.
Add the XA ADMINS group to the local Administrators group on the XA Server computer.
Create an XA Server Account
Create a user account in the domain with a User logon name of xaserver. This account can be named something else, but this document assumes that it is named xaserver.
Set the password for this account (this password will be used later in these instructions). Important: The password on this account must be set to never expire. If this password is allowed to expire, XA Server will stop working.
Add the xaserver domain user account to the local Administrators group on the XA Server computer. The xaserver user must be in the local administrators group on each server that XA will be installed on.
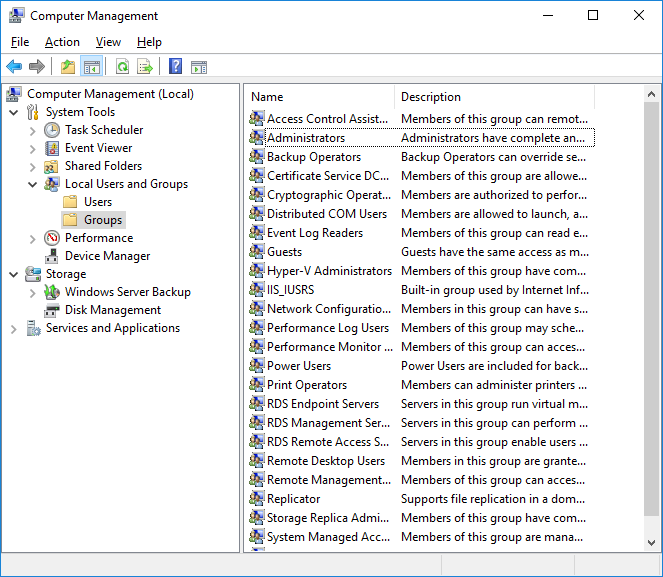
Go to Start > Administrative Tools > Computer Management to open the Computer Management window.
In the Computer Management window expand the Local Users folder. Then expand the Groups folder within it.
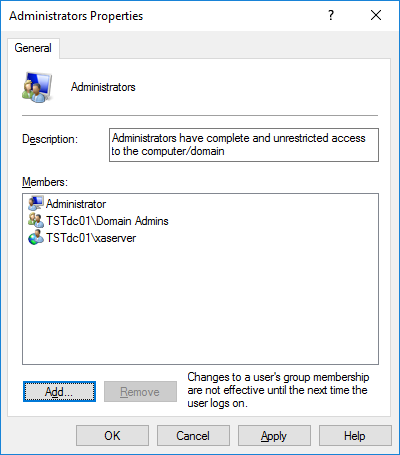
Double-click Administrators to open the list of members.
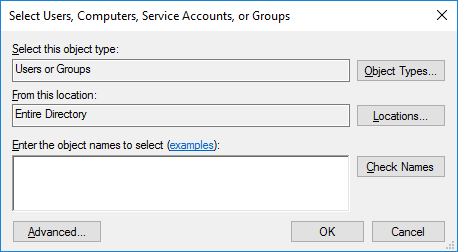
Click Add to add xaserver to the group.
Ensure that the proper location is selected and type xaserver in the text field. This could be the domain if there is more than one or it could be the Entire Directory as shown in the example.
Select OK. The xaserver user should now be visible as a group member.
Click OK and close the Computer Management window.
Run the XA Server Install File
Double-click the HealthCast ExactAccess Server.msi for Full SSO installation to open the wizard, then click the Next button on the ExactAccess Setup screen.
Note
Choose the correct installation file for the appropriate Configuration. Use HealthCast ExactAccess Server x64.msi (Full SSO).
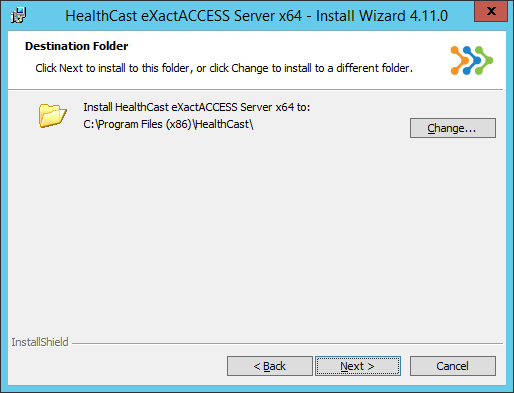
Click Next to continue. Click Change... to change the Destination Folder, if desired (we recommend that you use the directory path provided), then click Next to continue.
Note
The install path will automatically default to C:\Program Files (x86)\HealthCast\
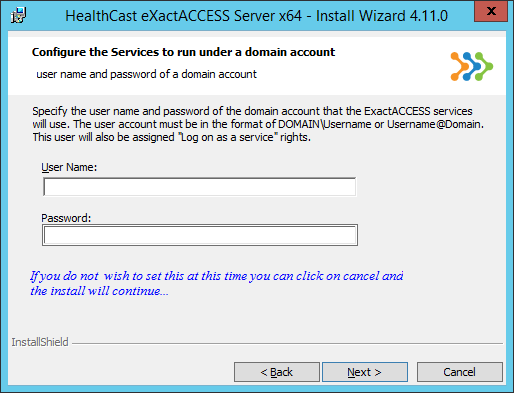
Fill in the username and password for the account that will be used for the ExactAccess services then click Next to continue or Click Cancel... the installation will continue without entering the username and password.
Note
If the domain account is used (xaserver is the account used in this guide) in this step it will not be necessary to Manually configure the services. As the, default settings configure the services for a Full SSO server installation. Selecting cancel will require the sevices be configured manually. See Manually enable XA Server Services and Manually Configuring Services Logon.
Click Install to begin the installation.
A status bar will appear to mark the progress of the install; click OK when the next dialog box appears indicating installation is complete.
Select No, I will restart my computer later.
Create and configure the Database(s) for the desired services
Using SQL Server Management Studio (or a similar tool), connect to the database server on which you wish to create the XA database.
Create a new database on the database server and name it. You may use a different name if you wish, but these instructions assume that the database name is xadb.
Use SQL Server Management Studio to open the file called Full XA database (MSSQL).sql. This file is included in the installation folder, typically: C:\Program Files\HealthCast\ExactAccess\SQL\<DB Server Type>\<XA Service>. Choose the appropriate version for the correct database server type from the folder.
In SQL Server Management Studio, select the xadb database and execute the Full XA database (MSSQL).sql file. This file will create objects in the xadb database. SQL Server Management Studio will indicate the query executed successfully.
Optional: Repeat the DB creation steps above for the ProxCard Server - HCProxCardScript.sql
Optional: Repeat the DB creation steps above for the auditSERVER - database.sql
Optional: Repeat the DB creation steps above for the HCIDeploy Server - MSSQL_2005.sql
Grant AD Account Permissions for the Database
You must grant the appropriate AD domain user account permissions to access and communicate with the new XA Server database. Please use the AD User account xaserver you created in the Active Directory step of the instructions.
In SQL Server Management Studio locate the server you have just installed XA Server on.
Under the server name, expand the Security folder.
Right click on the Logins folder and select New Login...
Ensure the Windows authentication radial button has been selected and enter the appropriate user name ( xaserver ).
Select User Mapping.
Check the box for xadb database then check the box for db_owner. Choosing the db_owner role prevents possible permissions problems from occurring in the future.
Select OK when you are finished.
Optional: Repeat the user permissions steps above for the ProxCard Server database
Optional: Repeat the user permissions steps above for the auditSERVER database
Optional: Repeat the user permissions steps above for the HCIDeploy Server database
Note
Note: If the user is already a member of the local Administrators group on the SQL Server, that user should already have permissions in excess of what is required to ensure proper operation of XA.
Server Service Dependencies
Note
This step can be skipped if the database servers are not installed on the XA servers in your configuration.
If SQL server has been installed on the same server as the ExactAccess server product, the services must be set to depend on the SQL service so that SQL server will start before the XA services request database operations.
Open the Registry Editor tool.
Locate the appropriate service name.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\HCExactAccessServer
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\HCauditSERVERService
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\hchidserverservice
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\hciployservice
Create the following registry name/value pair for each Key.
DependOnService: REG_MULTI_SZ = MSSQLSERVER
Manually enable XA Server Services
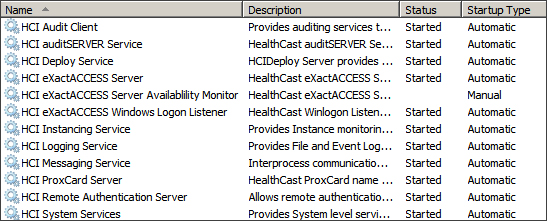
To enable services, open the Service Control Manager and scroll down to the section for HealthCast services. These services are prefixed with HCI and appear as a group. Choose the services that will be enabled in your environment and ensure that they are set for automatic startup.
HCI ExactAccess Server - This is the SSO application server. It provides SSO Services to client workstations.
This is a REQUIRED server service for SSO operation
HCI auditSERVER Service - This provides audit logging from client workstations and servers.
While this service is not required, it is highly recommended that this service be enabled and configured. It will provide data for reporting the usage of the XA servers, Connectors, and SSO functions in general
HCI ProxCard Server - This provides ProxCard services to client workstations.
This service is optional. If you do not have or plan to deploy Prox Card functionality within your organization, the service can be disabled
HCI Remote Authentication Server - This allows clients to perform remote authentication against the configured domain(s).
Remote authentication is useful for non-domain joined workstations (e.g. workstations in a workgroup) such as thin client devices that would otherwise not be able to authenticate domain account log-ins.
If you do not have non-domain joined workstations, and do not need to handle the password expiration warning for Kiosk Mode clients, this service can be disabled.
HCI Deploy Service - This provides Connector update (auto-update) functions for SSO enabled workstations.
HCI System Service - This provides various system level services to the ExactAccess product, such as obtaining the local system IP and MAC addresses for auditing.
This service should always be executed under the SYSTEM or NETWORK SERVICE user accounts
Optional Services
HCI ExactAccess Server Availability Monitor - allows e-mail notifications in the event the ExactAccess Server stops responding to user requests.
Failover notification can be handled by hardware failover devices. If you are using standard Windows Network Load Balancing (WLBS/NLB), you may want to configure and enable this service.
Configure which ExactAccess server services are monitored using the Server Configuration application.
Manually Configuring Services Logon
When using LDAP provider(s) (Either LDAP or LDAP + Global Catalog), the HCI ExactAccess Server Service must be configured with a domain account.
If using NT Integrated Security for MS-SQL for any of the following server functions, then each service must be configured with a domain account.
ExactAccess Server services (SSO) [HCI ExactAccess Server]
auditSERVER services [HCI auditSERVER Service]
ProxCard Server services [HCI ProxCard Server]
Deployment services [HCI Deploy Service]
If the organizations e-mail server requires authentication, and auditSERVER e-mail alerts are desired, it may be desirable to set the auditSERVER service [HCI auditSERVER Service] to run under a domain account so that a username/password do not need to be configured for alerts.
If domain policies have been put in place to restrict password change operations, it may be necessary to configure the HCI Remote Authentication Server to run under a privileged domain account.