Shell Replacement
When configuring Kiosk mode for passthrough authentication only, it is also possible to replace the Windows shell so that the normal Windows desktop (explorer.exe) is not launched, and is not available. This setting is intended to be used when the end point acts as a terminal to a remote session while retaining the badge tapping and session locking on the end point.
Tip
If you intend to launch SSO enabled applications or WebSSO applications, passthrough authentication cannot be used.
That means that shell replacement also cannot be used on the device, and is not a supported configuration.
The "Enable ExactAccess Shell" option replaces Windows Explorer desktop as the shell. Administrative users will be able to log into the workstation to perform administrative tasks. For this operation, ExactAccess will not launch, and the administrator will be presented with the Windows default desktop. Additionally, the Windows RUN keys will not be processed for the non-administrative users. This means that a new set of registry keys must be configured to properly launch the ExactAccess components for normal operation.
Shell Replacement
Shell replacement is supported in Locking Kiosk Mode only. It prevents users from having a Windows Desktop (explorer.exe) session on the workstation, severely limiting the scope of interaction with the local workstation. If the user needs to access local resources on the workstation, it is recommend that shell replacement NOT be used so that users are presented with a familiar system to use.
AppSense
Some portions of AppSense (such as user profile customization) will not function if the shell is replaced (e.g. not set to explorer.exe)
Please contact your AppSense representative for additional details about this requirement.
Windows 10
XA-2394,2402—Passthrough mode shell replacement, Explorer shell may not start the desktop when logging in as an administrator
Observed: When logging into Windows as an administrative user, the default shell (explorer) is started and the standard desktop is supposed to be displayed. However, instead of the Windows desktop, only a explorer file browser is launched with no desktop. UAC may prevent replacing the appropriate registry keys for the shell because the administrative user is forced to be recognized as a normal user which denies write access to the shell key.
Workaround: Modify the permissions on the following registry key:
HKLM\Software\Microsoft\Windows NT\current version\Winlogon
Add the specific administrator account(s) to the key and set full access.
Windows 10 requires a new procedure to function properly. See the Windows 10 requirements
To allow for enabling of the shell replacement, configure the operation in Passthrough authentication only mode.
Log-in as a Local Administrator to the workstation you would like to make changes on.
The Client Configuration Tool will only run under an account with Local Administrator privileges.
Navigate to the Windows® Start menu> All Programs > HealthCast > ExactAccess > Utilities > Configuration > Client Configuration.
and choose Operation.
Select one of the connection methods that are marked as installed. (Configure as necessary using the Configure... button.)
Select Kiosk Mode and ensure the "Enable ExactAccess Shell replacement" check box is checked. (it may be necessary to change modes to Kiosk Mode on the General tab if the device was not configured for Kiosk Mode during installation)
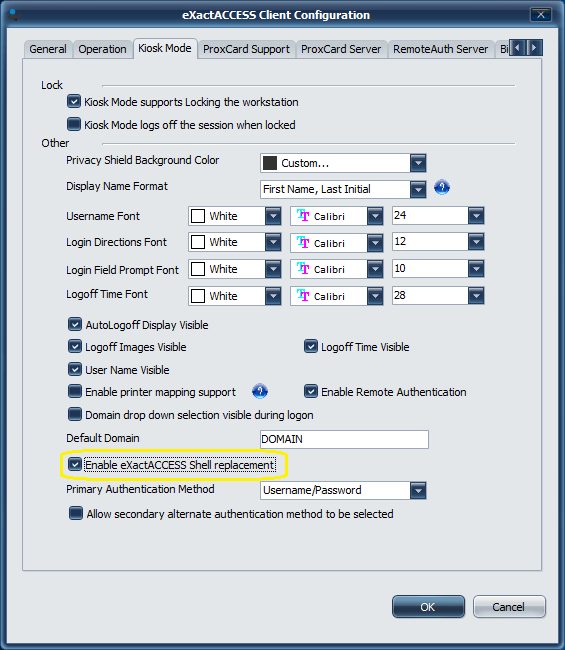
Click OK to apply the changes
Shell Replacement
The default setting as described above does not function for Windows 10. Additional configuration is required to fully enable Shell Replacement on Windows 10 systems.
For Windows 10: Modify the following PowerShell script as appropriate and run the script on the device.
Tip
This code cannot be used directly, as it shows you how to both enable and disable a custom shell via power shell script, as well as indicating the state of the configured shell. It must also be customized for your environment with your specific domain user accounts.
In addition, the power shell script has specific Windows 10 version release requirements. Please use the documentation provided by Microsoft to determine if your version of Windows 10 meets these requirements.
Powershell Script to enable Shell on Windows 10
# Check if shell launcher license is enabled function Check-ShellLauncherLicenseEnabled { [string]$source = @" using System; using System.Runtime.InteropServices; static class CheckShellLauncherLicense { const int S_OK = 0; public static bool IsShellLauncherLicenseEnabled() { int enabled = 0; if (NativeMethods.SLGetWindowsInformationDWORD("EmbeddedFeature-ShellLauncher-Enabled", out enabled) != S_OK) { enabled = 0; } return (enabled != 0); } static class NativeMethods { [DllImport("Slc.dll")] internal static extern int SLGetWindowsInformationDWORD([MarshalAs(UnmanagedType.LPWStr)]string valueName, out int value); } } "@ $type = Add-Type -TypeDefinition $source -PassThru return $type[0]::IsShellLauncherLicenseEnabled() } [bool]$result = $false $result = Check-ShellLauncherLicenseEnabled "`nShell Launcher license enabled is set to " + $result if (-not($result)) { "`nThis device doesn't have required license to use Shell Launcher" exit } $COMPUTER = "localhost" $NAMESPACE = "root\standardcimv2\embedded" # Create a handle to the class instance so we can call the static methods. try { $ShellLauncherClass = [wmiclass]"\\$COMPUTER\${NAMESPACE}:WESL_UserSetting" } catch [Exception] { write-host $_.Exception.Message; write-host "Make sure Shell Launcher feature is enabled" exit } # This well-known security identifier (SID) corresponds to the BUILTIN\Administrators group. $Admins_SID = "S-1-5-32-544" # Create a function to retrieve the SID for a user account on a machine. function Get-UsernameSID($AccountName) { $NTUserObject = New-Object System.Security.Principal.NTAccount($AccountName) $NTUserSID = $NTUserObject.Translate([System.Security.Principal.SecurityIdentifier]) return $NTUserSID.Value } # Get the SID for a user account named "kms". Rename "kms" to an existing account in your domain to test this script. $Cashier_SID = Get-UsernameSID("kms") # Define actions to take when the shell program exits. $restart_shell = 0 $restart_device = 1 $shutdown_device = 2 # Examples. You can change these examples to use the program that you want to use as the shell. # This example sets the HCIShell as the default shell, and restarts the device if the shell application is closed. $ShellLauncherClass.SetDefaultShell("c:\program files (x86)\healthcast\exactaccess\hcishell.exe", $restart_device) # Set Explorer as the shell for administrators. $ShellLauncherClass.SetCustomShell($Admins_SID, "explorer.exe") # View all the custom shells defined. "`nCurrent settings for custom shells:" Get-WmiObject -namespace $NAMESPACE -computer $COMPUTER -class WESL_UserSetting | Select Sid, Shell, DefaultAction # Enable Shell Launcher $ShellLauncherClass.SetEnabled($TRUE) $IsShellLauncherEnabled = $ShellLauncherClass.IsEnabled() "`nEnabled is set to " + $IsShellLauncherEnabled.Enabled # Remove the new custom shells. $ShellLauncherClass.RemoveCustomShell($Admins_SID) $ShellLauncherClass.RemoveCustomShell($Cashier_SID) # Disable Shell Launcher $ShellLauncherClass.SetEnabled($FALSE) $IsShellLauncherEnabled = $ShellLauncherClass.IsEnabled() "`nEnabled is set to " + $IsShellLauncherEnabled.EnabledThis code snippet is taken directly from the Microsoft Web Site for enabling different shells for different user classes (administrators vs. normal users). It has only been modified as an example of which user to configure, and the name of the shell to set for the generic user. It may need to be adjusted for each workstation if the generic user is unique per workstation.
For additional information on how to enable shell replacement, please use the documentation provided by Microsoft.
Remove all registry keys from Windows|RUN registry location that pertain to ExactAccess so that when an administrative user logs in and explorer.exe launches as their shell, XA processes do not run.
Custom Start Registry Keys
To customize the startup application values, open regedit and navigate to the following registry key:
HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess\startup
There are several values that are pre-populated, but can be adjusted for optimal performance:
The AutoLogoff.exe entry [02] may be removed as the client is configured for Kiosk Mode.
An entry for hciNetStatus.exe may be added (in place of autologoff [02]) as the client is configured for Locking Kiosk mode, so that the network status display appears on the Privacy Shield.
To enable, add 02:reg_sz="c:\program files (x86)\healthcast\ExactAccess\hciNetStatus.exe" hcikmlock