HCI Deploy
Communications
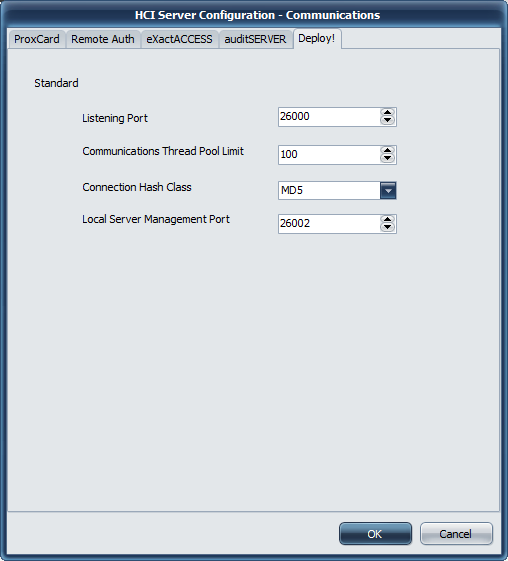 |
Communications Settings
Listening Port
Port 26000 is used as the port for ExactAccess clients that dynamic protocol negotiations. If this port is updated on the server, a corresponding update must be made to the client workstations using this server.
Communications Thread Pool Limit
This protocol allows for selecting the thread cache limit for connections to help improve performance. The default 200 is sufficient for most installations, but can be configured as needed in high load environments, or may be lowered for low load environments. The number specified here means that the server will (pre)allocate this number of threads in the server process to handle incoming requests.
Connection Hash Class
The available options are MD5 and WHIRLPOOL.
MD5 is a lightweight hash algorithm that generates 128 bit hashes, but is only recommended if the client workstations connecting to the system are slow (less than 2GHz).
WHIRLPOOL is a hash algorithm that generates 512 bit hashes. The larger number of bits means it is more secure, but it also requires slightly more CPU cycles to generate. WHIRLPOOL is the recommended choice if your workstations are 2GHz or better.
Warning
Not all HealthCast products support the Whirlpool hash algorithm. Ensure that the client product you are deploying supports the feature configuration for the server.
Local Server Management Port
This is the port bound to only the local address (127.0.0.1 or ::1) that the ExactAccess Server Monitor tool will use to query server status of the service.
Database
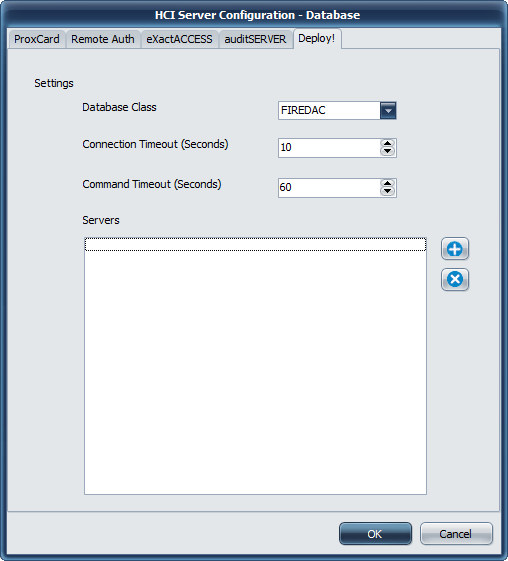 |
Database Settings
Database Class
The only available database provider for this version of ExactAccess server services is FireDAC. It provides connectivity to Microsoft SQL Server using Microsoft Native Drivers or Microsoft SQL ODBC drivers.
Connection Timeout
This indicates how long the drivers will wait for a successful connection to a SQL server. If this ExactAccess installation will be using service database fail-over connection strings (multiple database connection strings are configured for the service), this number should be set as low as possible to improve fail-over responsiveness to secondary connections. For high availability configurations (SQL clustering, Active Group Listener configurations), this number should be set high enough for the drivers to allow clustering fail-over logic to promote a SQL server to the active state when the primary server has failed and not immediately return a connection failure to the service.
Command Timeout
This indicates how long any single transaction made by the service can take to complete. For highly stressed SQL servers, this number should be configured to allow for the appropriate workload to be completed even if the server is at maximum capacity. If there is excess capacity on the server, all service operations are expected to take less than 10 seconds to complete for normal operations.
Database Encryption Class
For those server services that support updated database encryption, choose an encryption method to use to protect the data. During upgrades, choose the LEGACY or PROX_LEGACY option. After upgrade has been completed for all servers, choose a method other than LEGACY or PROX_LEGACY. AES192 is recommended, but any of the other options are valid. Consult your security officer for recommendations for your organization.
Important
During an upgrade scenario, the first server to be upgraded should be considered the "master" server. From this server, click the EXPORT button to save the auto-generated database encryption keys for each of the services (SSO and Prox) and save them to separate files (ProxDBKeys.key and XADBKeys.key) - provide a password to protect these files when prompted. It is a good idea to have more than one person export these keys, and keep them in a secure offsite location for disaster recovery.
Once these keys have been exported, they will need to be imported on each of the servers during the upgrade.
To import the keys to an existing server, Open the configuration tool, select Database, then choose the appropriate TAB (Prox or SSO/ExactAccess). Click the IMPORT button. Locate the correct file (ProxDBKeys.key for ProxCard, XADBKeys.key for SSO/ExactAccess keys) and click OK to open the file. Provide the password used to secure the exported keys. A message will indicate the success or failure of the import. Repeat this step for each server to be upgraded.
Servers
This lists the currently configured connection string for each configured SQL server in the organization. The ExactAccess server services support as many fail-over connection strings as desired. The first connection string entered in this list will be considered the primary server. The remaining servers listed will not be utilized unless the primary server Connection Timeout is reached and the server is deemed off-line. In primary server fail conditions, each of the servers will be attempted in the order in which they are entered in this list until a connection is made or all servers have been attempted and an error is returned to the client
Adding a new connection
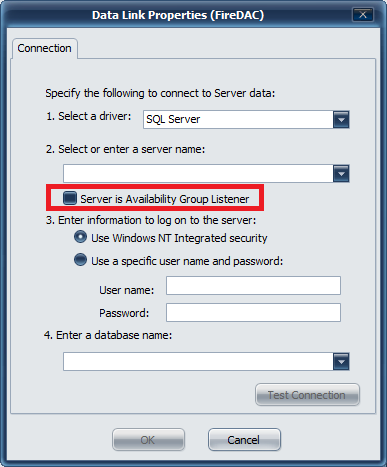
Click the plus ( ) button to bring up the Data Link Properties (FireDAC) window
) button to bring up the Data Link Properties (FireDAC) window
 |
Connections
Select a driver
Microsoft provides several connectivity drivers for SQL server. You may choose SQL server as the driver (which is available by default on Windows 2012 R2 and above) - or optionally, install one of the later Microsoft SQL Server Native Drivers which will provide other connectivity options (such as ODBC)
Info
it may be necessary to install the Native SQL drivers. This is typically only necessary for Windows 2008 R2, but newer SQL drivers may also improve performance. See the note below on downloading an appropriate driver.
Driver Download
Check with the Microsoft Site for newer or additional drivers for supporting the latest versions of SQL server.
Select a server (by using the browsing service) or manually enter a SQL server database name and instance.
If this SQL server is part of the High Availability Group configuration (available in SQL server 2012 and above), check the box for Server is Availability Group Listener. This will notify the Microsoft Driver to expect multiple IP addresses from multiple SQL servers configured in this group/cluster so that the driver can provide appropriate fail-over if the primary node fails.
Authentication Type
If the service has been configured to run under a service account, that service account must have been granted DB Owner permissions for the service database (SSO, Prox, Deploy, Audit) when choosing to use Windows NT Integrated Security. In this case, a password does not need to be supplied in this configuration, as the security credentials are configured on the service using MMC services management tools provided by Windows.
Warning
When choosing to use Windows NT Integrated security during configuration, please note that the user account to launch the tool MUST match the account that is to be used for authentication to ensure the proper permissions and connectivity tests can be completed. The tool also requires UAC elevation, so this user must also be a local administrator on the server for configuration to be completed.
If you choose to use SQL server authentication, then pick the "Use a specific user name and password" that has been configured in SQL server as the DB owner of the service database (SSO, Prox, Deploy, Audit). This username and password will become part of the connection string and will be stored encrypted in the registry.
Enter a database name
Manually type if the name for the database associated with this service, or click the drop down to show a list of available databases to connect to.
Warning
If the current user (that the tool is running under) does not have access to the SQL server, the browse function will fail, as the tool is unable to connect to the SQL server with the current user. This is only applicable when using Windows NT Integrated Security.
When using SQL server authentication by supplying a user name and password, the browse feature for the database will only fail if the user has not been granted access to any databases, or the account information is not valid.
Other
 |
Other Settings
There are no additional features or configuration for the HCI Deploy service.
Configuring Workstation Age
Workstations that have not checked into the HCIDeploy server for an extended period of time are automatically removed from the database. This length of time can be configured as follows:
Using RegEdit, adjust the following registry key:
HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\HCIDeployServer
MaxAgeInDaysForValidWorkstations: reg_dword = <max days at which the workstation will be removed>
Note
If the key/value does not exist, the default is 30 days. To return the server to use the default value, either enter 30 for the value, or delete the name/value pair.
Warning
Ensure the service is stopped before adding this key if it does not exist.
Always use a value > 0 when defining this setting. A value of 0 will remove all workstations every time the service runs a cleanup.
