Roaming Sessions
Session disconnection timings (i.e., "lock") and session active timings (i.e., "logoff") are controlled by Terminal Server or Citrix settings, which are set independent of an ExactAccess installation. Terminal Server/Citrix may be configured to automatically disconnect a session after a specified period of inactivity. This will leave the user's session available (though disconnected) to be reconnected to at a later time (i.e., to "roam a session"). Terminal Server/Citrix may also be configured to log a user's session off after a specified amount of inactivity, independent of the connection time.
Optionally, if it is preferable to use the ExactAccess timings to control disconnecting and logging off inactive sessions, you may do so by ensuring that autologoff.exe is in the Windows RUN key (for published Windows Desktops), and the registry setting AutoLogoffEnabled is set to 1 (see Access Scenarios below for more information on using autolgoff)
Configurable Workflow Scenarios
By default, users connecting to a Citrix server will see the desktop configured in this registry key:
HKLM\Software\HealthCast\ExactAccess\XAServerManager\Desktop
The following scenarios are also supported:
Published Windows desktop where explorer.exe is running. When a user logs in, the HCXACitrixDesktop will execute and display the user's application desktop.
Published XA desktop where explorer.exe is not running. When a user logs in, they will not receive a desktop. To configure this scenario, publish the application XAUCM.exe (i.e. "C:\Program Files\HealthCast\ExactAccess\XAUCM.exe"). This scenario is used in conjunction with full published Windows Desktops for remote users, and published applications for local users in the organization who utilize the same Citrix servers. Local users may already have an XA desktop for the workstation and do not want a second XA desktop appearing from the Citrix server. Remote users will have a full Windows desktop and therefore need access to the XA Desktop.
Published connectors where XAUCM.exe and explorer.exe are not running. When a user logs in, they will not receive a desktop.
Published XA Desktop where explorer.exe is not running. When a user logs in, they will receive the configured desktop. To configure this scenario, publish the application HCXACitrixDesktop.exe (i.e. "C:\Program Files\HealthCast\ExactAccess\HCXACitrixDesktop.exe"). This scenario is used when local workstations do not display an XA desktop, but connect to a Citrix server to display SSO-enabled applications. The user does not receive a full Windows desktop and all applications appear local (Citrix Seamless published applications).
Published Desktops and Application Access
There are several methods to provide access to SSO enabled applications in your environment. The following information may help to show how ExactAccess can be configured to accommodate these scenarios.
Access Scenarios
All users are accessing a published Windows Desktop.
All users are accessing a published XA Desktop.
All users are accessing published connectors.
Mixed environment where users outside the firewall are accessing published Windows Desktop or a published XA Desktop, users inside the firewall are accessing a published XA Desktop or published connectors.
Per-Session Inactivity timeouts
It is now possible for each user session to have a customized lock and logoff timeouts independent of other users timeouts by modifying the following keys in the users/session profile registry:
HKEY_CURRENT_USER\Software\HealthCast\ExactAccess
LockTimeLimit: reg_dword = 60
LogoffTimeLimit: reg_dword = 240
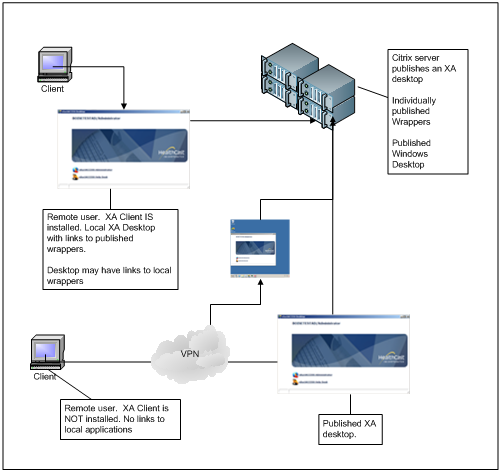
Mixed Published Environment
A mixed environment where remote users outside of the organizational firewall need access to a full Windows session including an XA desktop, but users inside the firewall will be accessing published XA desktops, or wrappers. This configuration allows the greatest flexibility on end user application display and executing both local (on the workstation, inside the firewall) and remote (on the Citrix server) applications.
Operation
The remote application operates as an isolated Windows user session.
Multiple applications may or may not share the same session.
Session management is handled by terminal server or Citrix sessions.
Session Lock and Logoff times are configured via terminal server or Citrix settings, however, they can also be controlled by ExactAccess settings.
The end user receives a single XA desktop running on the Citrix Server.
Graceful Logoff is handled by ExactAccess (WatchForLogoff.exe or AutoLogoff.exe)
Full Windows desktop publishing is supported
In order for Citrix session timeouts to be handled properly for Graceful Logoff, it is necessary for WatchForLogoff.exe to be running in the remote session.
Create a batch file to launch the following items:
Tip
c:\program files\HealthCast\ExactAccess\watchforlogoff.exe
c:\program files\HealthCast\ExactAccess\XAUCM.exe
Publish this batch file as an application and configure the appropriate session timeouts using the Citrix or Terminal Server tools and settings.
This mode of operation publishes the XA desktop to display links to the SSO enabled applications on the server. It should not be used when desiring access to local (end-point) application access. Instead, use directly published Wrapper links.
In order for ExactAccess session timeouts to operate, it is necessary for autologoff.exe to be running in the remote session.
Create a batch file to launch the following items:
Tip
c:\program files\HealthCast\ExactAccess\autologoff.exe
c:\program files\HealthCast\ExactAccess\XAUCM.exe
Enable the following registry key:
Tip
HKEY_LOCAL_MACHINE\Software\HealthCast\ExactAccess
AutoLogoffEnabled: reg_dword = 1
Configure the appropriate lock and logoff time settings by using the Client Configuration tool on the Citrix server.
Publish this batch file as an application
Tip
This mode of operation publishes the XA desktop to display links to the SSO enabled applications on the server. It should not be used when desiring access to local (end-point) application access. Instead, use directly published Wrapper links.
Published Connectors
Publishing a connector directly from the server and NO XA Desktop is present on the server (it may be available on the client (end-point device)). The client is responsible for providing the SSO enabled links to the applications, and the server will not present an XA desktop. This scenario is similar to published XA desktop, however, since no XA desktop is presented from the Citrix server, it is not necessary to publish the batch file. Instead, the individual connector applications are published from the Citrix server, and are launched via links on the XA desktop running on the client (end-point) machine where the XA client is installed, or by another means such as Citrix Web Interface or Windows application links.
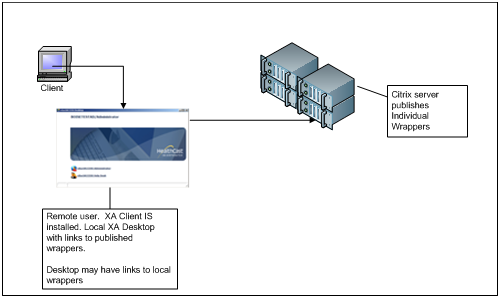
This scenario is intended for environments where both local applications and remote applications are desired, and the XA desktop will be launched from the client workstation with links to both. In addition, this mode of operation is supported on client workstations where XA is NOT installed, but links to NON-SSO enabled applications on the end-point device must be provided by other means.
Operation
The remote application operates as an isolated Windows user session.
Multiple applications/connectors may or may not share the same session.
Session management is handled by terminal server or Citrix sessions.
Session Lock and Logoff times are configured via terminal server or Citrix settings.
The end user receives a single XA desktop running on the end-point device.
Graceful logoff is handled by the individual connectors.
Published Desktop
A full published Windows Desktop is presented to the end user. All applications run on the Remote Citrix/Terminal Server. Explorer.exe runs to present the Windows Desktop. This is the standard configuration installed with RSM and is the expected mode of access to SSO enabled applications. No further configuration must be done to support this scenario. This scenario allows access from RDP and Terminal Services because it presents the full Windows Desktop. Additionally, this is supported from Citrix via ICA as well as RDP. The remote desktop session typically expands to full screen on the local workstation, and the end user operates exclusively with the remote Windows session.
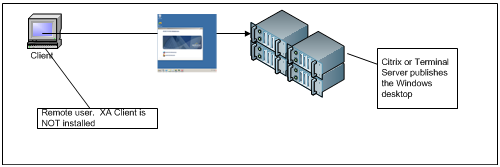 |
Client workstations can access the full Windows published desktop in a variety of ways:
Remotely through Terminal Services (RDP) or Citrix Web Interface (both inside and outside the firewall)
By using eXpressACCESS inside the firewall on thin devices.
By using Citrix receiver auto-launched from a workstation where XA client is installed, but configured to NOT display a local XA desktop.
Operation
The remote application operates as an isolated Windows user session.
Session management is handled by terminal server or Citrix sessions.
Session Lock and Logoff times are configured via terminal server or Citrix settings, however, they can also be controlled by ExactAccess settings.
If using ExactAccess settings, enable the following registry key:
Tip
HKEY_LOCAL_MACHINE\Software\HealthCast\ExactAccess
AutoLogoffEnabled: reg_dword = 1
The end user receives a single XA desktop running on the Citrix Server.
This mode of operation is nearly indistinguishable from a standard, local Windows workstation.
Graceful logoff is handled by ExactAccess (watchforlogoff.exe)
All applications share the same session.
Interactive Installation
Tip
ExactAccess client supports both 32-bit and 64-bit operating system. Choose the appropriate installation MSI for the operating system target:
for 32-bit clients: HealthCast ExactAccess Client.msi (not supported for Roaming Sessions installations)
for 64-bit clients: HealthCast ExactAccess Client x64.msi
Run the MSI
Adjust install directory if desired
Click Install
Confirm UAC if prompted
Client Configuration Tool will start when the install is complete
If Roaming Sessions Mode is not displayed, select Change Mode button and choose Standard Mode
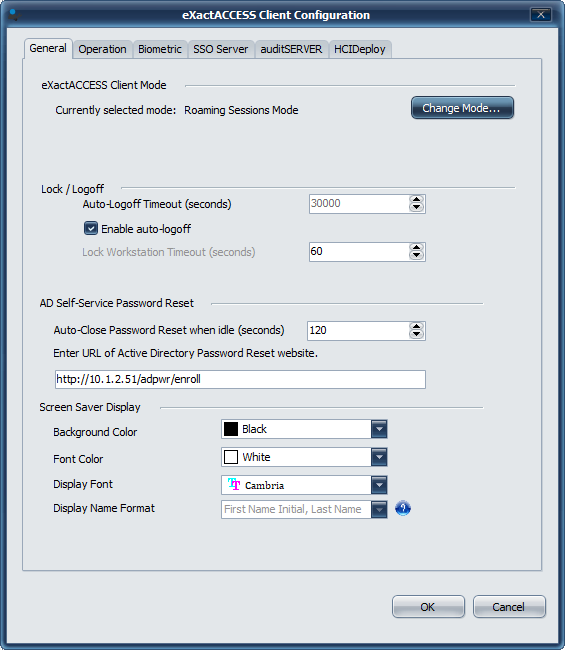
Select Operation Tab
Choose Full SSO
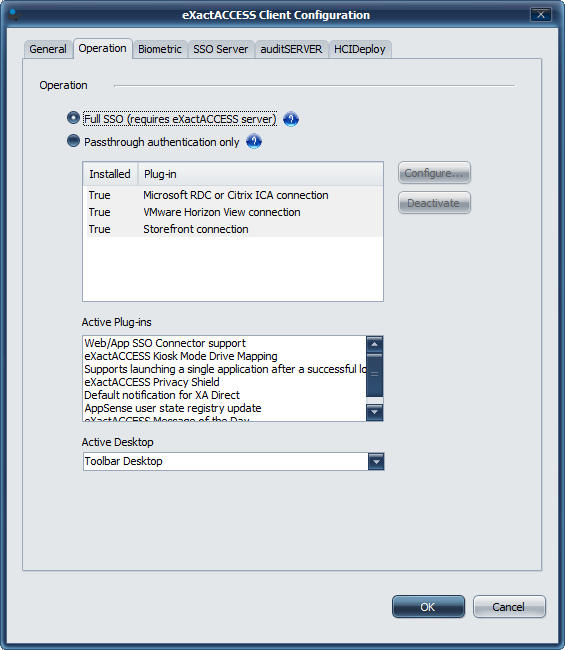
Ensure that all appropriate server connectivity information is provided under each of the server tabs.
After UI configuration is complete, select Finish and reboot the workstation when prompted.
Installation command line parameters for Roaming Sessions configuration
From an administrative command prompt (or remote deployment package), execute the ExactAccess client install with the appropriate command line parameters.
Set kiosk mode: XA_MODE=RSM
Set the servers: XA_SRV=<name of server>
Set to use auditSERVER: XA_AUDIT_SRV=<name of server>
Set to use Deploy server: X_D_SRV=<name of server>
Set workstation deployment group: X_D_GRPS=<groups to add workstation to in HCIDeploy>
(optional) Enable Autologoff: XA_ALE=1
(optional) Set autologoff time in seconds: X_KM_AL_TIME=600
(optional) Set the lock (or disconnect) time in seconds: X_KM_LTL=300
Disable running configuration tool after install/upgrade: X_RUN_CONFIG=0
msiexec /i "HealthCast ExactAccess Client x64.msi" XA_MODE=RSM XA_SRV=myServer XA_AUDIT_SRV=myServer X_D_SRV=myServer X_D_GRPS=Roaming X_ALE=1 X_KM_AL_TIME=240 X_KM_LTL=60 X_RUN_CONFIG=0 /qn
Registry Settings
Parameter Name | Applicable Modes | Registry Keys Affected | Value | Setting Description |
|---|---|---|---|---|
XA_SRV | ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess\Servers\INDY 0000: reg_sz | Valid Server NETBIOS or FQDN Name or IP address | Primary XA (SSO) server name |
XA_AUDIT_SRV | ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\AuditServerClient\Connection\INDY 0000: reg_sz | Valid Server NETBIOS or FQDN Name or IP address | auditSERVER name |
XA_PRX_SRV | ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ProxCardClient\Indy 0000: reg_sz | Valid Server NETBIOS or FQDN Name or IP address | Prox Card Server Name |
X_D_SRV | ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\HCIDeployClient\Indy 0000: reg_sz | Valid Server NETBIOS or FQDN Name or IP address | HCIDeploy server name |
X_RA_SRV | KM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\HCCitrixSessionDirectory\INDY 0000: reg_sz | Valid Server NETBIOS or FQDN Name or IP address | Remote Authentication Server name |
X_PREF_IPV4 | ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ProxCardClient PreferIPv4: reg_dword HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess PreferIPv4: reg_dword HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\AuditServerClient PreferIPv4: reg_dword HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\HCCitrixSessionDirectory PreferIPv4: reg_dword HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\HCIDeployClient PreferIPv4: reg_dword | 1 | Indicates that any TCP/IP communication prefers to use IPv4 when IPv6 is installed and available This setting will be ignored if the *_SRV setting(s) listed above contain a direct IPv6 address. |
Parameter Name | Applicable Modes | Registry Keys Affected | Value | Setting Description |
|---|---|---|---|---|
X_SP | ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess\Servers\INDY Port: reg_dword | 15001 | Communications port for XA (SSO) server |
ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess\Servers\INDY EnabledServerIDs: reg_sz | 0000 | Enabled Servers List. Comma delimited list of server identifiers 0000,0001,0002, etc. | |
XA_EC | ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess\SocketTransport\Indy Encryption: reg_sz | RIJNDAEL | Encryption Class: RIJNDAEL, RIJNDAEL128, RIJNDAEL256, BLOWFISH, BLOWFISH256, TWOFISH, SERPENT |
XA_CC | ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess\SocketTransport\Indy Compression: reg_sz | VCLZIP | Compression Class: NONE, VCLZIP |
Parameter Name | Applicable Modes | Registry Keys Affected | Value | Setting Description |
|---|---|---|---|---|
ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\AuditServerClient\Connection\INDY SocketPort: reg_dword | 25000 | Communications port for auditSERVER | |
ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\AuditServerClient\Connection\INDY EnabledServerIDs: reg_sz | 0000 | Enabled Servers List. Comma delimited list of server identifiers 0000,0001,0002, etc. | |
ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\AuditServerClient\Connection\INDY EncryptionClass: reg_sz | NONE | Encryption Class: RIJNDAEL, RIJNDAEL128, RIJNDAEL256, BLOWFISH, BLOWFISH256, TWOFISH, SERPENT | |
ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\AuditServerClient\Connection\INDY CompressionClass: reg_sz | VCLZIP | Compression Class: NONE, VCLZIP |
Parameter Name | Applicable Modes | Registry Keys Affected | Value | Setting Description |
|---|---|---|---|---|
X_D_PORT | ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\HCIDeployClient\Indy Port: reg_dword | 26000 | Communications port for HCIDeploy |
ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\HCIDeployClient\Indy EnabledServerIDs: reg_sz | Enabled Servers List. Comma delimited list of server identifiers 0000,0001,0002, etc. | ||
X_D_EC | ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\HCIDeployClient\Indy EncryptionClass: reg_sz | RIJNDAEL | Encryption Class: RIJNDAEL, RIJNDAEL128, RIJNDAEL256, BLOWFISH, BLOWFISH256, TWOFISH, SERPENT |
X_D_CC | ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\HCIDeployClient\Indy CompressionClass: reg_sz | VCLZIP | Compression Class: NONE, VCLZIP |
X_D_PORT_CRM | ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\HCIDeployClient\Indy ClientPort: reg_dword | 26100 | Communications port for HCIDeploy remote management |
X_D_GRPS | ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\HCIDeployClient DefaultGroups: reg_sz | Default Locations the workstation should be registered in. (When the service starts, it will register these location names, then remove the setting) | |
X_D_RM | ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\HCIDeployClient\Indy EnableRemoteManagement: reg_dword | 1 | Enable(1) or Disabled(0) management port. If this setting is disabled, the HCIDeploy Console will not be able to display the deployed package state on the workstation |
X_D_HID | ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\HCIDeployClient\Indy ConfiguredHashID: reg_sz | {A439AF92-98CD-4C20-83AC-5FD12308F51A} | Indicates the communications hash ID the remote management listening port requires for encryption handshake: MD5 (128 bit) GUID: {A439AF92-98CD-4C20-83AC-5FD12308F51A} WHIRLPOOL (512 bit) GUID: {C86DDD9B-09B2-4360-878B-F5D3B6997CDE} |
X_D_SCH | ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\HCIDeployClient\Schedule Schedule: reg_sz | Schedule information string indicates how often the client will check in with the server to determine if a package update or uninstall is needed on the workstation | |
ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\HCIDeployClient\Indy ConnectionTimeout: reg_dword | 1 | The time in seconds that the client will attempt to connect to the all of the configured servers before returning an error to the client for a connection failure. |
Parameter Name | Applicable Modes | Registry Keys Affected | Value | Setting Description |
|---|---|---|---|---|
XA_N_BREQ | ALL | HKEY_LOCAL_MACHINE\SOFTWARE\Identity Automation\XANotification BindingRequest: reg_sz | tcp://127.0.0.1:6226 | The port specified 6226 can be adjusted if necessary. NoteThe Windows (or other) Firewall may also need to be adjusted to allow network communication on this port for proper communication on the local machine between the XA client and the Browser Plug-in. The port must match what is used in |
XA_N_BRESP | ALL | HKEY_LOCAL_MACHINE\SOFTWARE\Identity Automation\XANotification BindingResponse: reg_sz | tcp://localhost:6226 | The port specified 6226 can be adjusted if necessary. NoteThe Windows (or other) firewall may also need to be adjusted to allow network communication on this port for proper communication on the local machine between the XA client and the Browser Plug-in. The port must match what is used in |
XA_ALE | ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess AutoLogoffEnabled: reg_dword | 1 | Enables (1) or Disables (0) idle session logoff. Logoff only occurs after the session has locked. |
X_KM_AL_TIME | ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess LogoffTimeLimit: reg_dword | 600 | The number of seconds the session can be idle (locked) before the session will be logged off. |
X_KM_LTL | ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess LockTimeLimit: reg_dword | 300 | The number of seconds a session can be idle before the session is automatically locked |
X_PRA | SUM,KM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\PasswordReset URL: reg_sz | Password Reset URL to a web site than allows a user to reset their domain password (such as ADPWR) | |
X_ACT | SUM,KM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\PasswordReset AutoCancelTime: reg_dword | 120 | The auto cancel time for inactivity of the password reset web display in seconds. |
ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess ShowXAStatusMessages: reg_dword | 1 | When Enabled (1) Allows XAUCM to display the status message during startup, show desktop, and shutdown. These status messages will not be shown when Disabled (0) | |
ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess SkipLoadingAppList: reg_dword | When Enabled (1) Indicates that XA should not load the application list during login to improve performance. When Disabled (0), XA will load the users application list from the server. TipThis setting is required to be Disabled (0) if the user will launch SnapApp enabled applications (either Windows or Web) on the system where the setting is set. Also, if the ExactAccess Desktop will be displaying applications on the workstation, this setting must be Disabled (0) so the users authorized applications will be loaded for presentation. Not all workstations require this setting to be disabled - for instance, in a Published Application scenario, this setting can be enabled on the RSM server if the user will launch WebSSO or Windows SnapAPP applications on their local workstation and use published connectors for applications on the RSM server. This setting can also be Enabled (1) when using the Kiosk Mode Passthrough configuration, as the desktop presentation will be handled by an RSM or VDI desktop (remote session), so the local workstation does not need to retrieve the application list. | ||
ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess BeepBeforeLockEnabled: reg_dword | Enables (1) or Disables (0) a system beep during the about to lock countdown | ||
ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess LockBeepIntervalInSeconds: reg_dword | This value is how many seconds occur between each beep during the countdown before lock. | ||
ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess LockBeepStartTimeInSeconds: reg_dword | This value is how many seconds before lock does the beep notice start to occur. It also indicates when the visual status will indicate the system is about to lock. | ||
ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess LockBeepIndex: reg_dword | 32 | May be one of the following values 0 - play sound associated with Default Beep sound in the Sound Scheme 16 - play sound associated with Critical Stop sound in the Sound Scheme 32 - play sound associated with Question sound in the Sound Scheme 48 - play sound associated with Exclamation sound in the Sound Scheme 64 - play sound associated with Asterisk sound in the Sound Scheme 4294967295 - use PC Speaker beep instead of scheme sound TipNote that the user may not have a .WAV file associated with the Sound Scheme values listed. Verify with the Sound Scheme that each of the items identified is associated with a .WAV file. These values can be found under: HKEY_CURRENT_USER \AppEvents \Schemes \Apps \<Type> \.Current -- (Default) Where <Type> is one of the following values: .Default, SystemHand, SystemQuestion, SystemExclamation, SystemAsterisk | |
X_LDM | ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess KMLockDisplayMode: reg_dword | 5 | Change how the user name is displayed in the Active User List, Privacy Shield, and the XA Desktop 0 - Full Name* 1 - Last Name only 2 - First Name Only 3 - Directory Service Name ** 4 - Initials Only 5 - First Name, Last Initial 6 - First Initial, Last Name 7 - "In use" only ** 8 - No user name display ** 9 - Full First Name and Full Last Name *** 10 - Full First Name Only *** 11 - Full Last Name Only *** 12 - Full First Name, Last Initial *** 13 - Full First Name Initial, Full Last Name *** Warning* Full Name is the First + Last, or Display Name field, depending on how the server is configured. *** - Full First Name and Full Last Name are not parsed from username properties, but are passed directly from the server. Warning** In Passthrough configuration, only values 3,7,8 are valid. ** Optionally, in Kiosk Mode, The user name can be removed from the privacy shield with the PSLoginNameVisible setting (allowing the name to remain showing on the XA Desktop) |
ALL | HKLM\Software\HealthCast\ExactAccess\Override LogoffOnDesktopClose: reg_dword | Enables (1) or Disables (0) initiating logoff if the user closes the Application Desktop (not valid for Toolbar Desktop) | ||
ALL | HKLM\Software\HealthCast\ExactAccess\Override ShowDesktopOnLogoffCancel: reg_dword | Enables (1) or Disables (0) initiating re-launching the XA Application Desktop (not valid for Toolbar Desktop) if the user cancels logoff | ||
ALL | HKLM\Software\HealthCast\ExactAccess\Display DesktopStyle: reg_sz | hcgreen.vsf | The visual style file applied to change the look and feel of the XA Toolbar Desktop (not valid for Application Desktop). | |
XA_DSK_CLASS | ALL | HKLM\Software\HealthCast\ExactAccess\XAServerManager Desktop: reg_sz | AppDesktop.clsAppDesktop | AppDesktop.clsAppDesktop: also referred to as Application Desktop, launches an application window similar to a web page that lists the user's SSO enabled applications as well as "lock" and "logoff" buttons. NoDesk.clsNoDesk: also referred to a No Desktop, does not launch an XA Desktop when XA is started. xatbdesk.clsxatbdesk: also referred to as Toolbar Desktop allows for the XA Menu to appear as a popup/context menu from the XA Taskbar icon. Additionally, a secondary application can be launched that looks and acts like the standard Windows task/start bar in that it will display favorite applications and has a start button to display a popup menu of applications with a work space similar to Windows 10. HCCitrixDesk.clsDesktop is a specialized desktop presentation used when the same Citrix server publishes a full Windows desktop and the user should see an XA menu of SSO enabled applications. The same Citrix server may also be used to publish xa directly but have the nodesktop option so an xa desktop does not appear. RequiredWhen using the XATBDesk.clsXATBDesk class, it is necessary that the DESKTOP_SERVER.XML be registered with the XA server before it will function. See Registering application XML files in the ExactAccess Administrator. |
All | HKLM\Software\HealthCast\ExactAccess\XAServerManager ClientDSProgID | NoteThis setting must be manually updated after an installation on RSM to use the virtual channel class to retrieve the current XA user from the end point device. Using the Client Configuration tool may reset this value when saving settings. WarningThis setting may not be set during the install or with a transform. | Class that determines where the user identification is retrieved from. NTClientDSUser.clsNTClientDSUser (SUM,RSM,VDI) hciVCCred.clshciVCCred (RSM ONLY) NTKMDSUser.clsNTKMDSUser (KIOSK ONLY) | |
X_ALA_CHK | ALL | HKLM\Software\HealthCast\ExactAccess\AutoLaunch CheckAccess: reg_dword | 0 | This setting determines whether an access check should be performed before the application is auto-launched. If the value is set to zero (0), the application will be launched and is not required to be registered in XA. The user logging in does not have to be granted access to launch the application. If the value is set to one (1), the application must be registered in XA and the user must belong to a role that has been granted access to the application. |
X_ALA_PATH | ALL | HKLM\Software\HealthCast\ExactAccess\AutoLaunch Launch: reg_sz |
Published XA Desktop
A published XA desktop where explorer.exe is not running, designed to reduce session resource requirements because the user does not need a full Windows environment. When a user logs in to the Citrix environment, they do not receive a desktop on the LOCAL machine, but they do receive a REMOTE XA desktop that appears to be running locally (as a standard Citrix published application in seamless mode). This mode of operation works well in mixed environments where the user will run applications on the local workstation as well as the remote server. The ExactAccess client may or may not be installed on the local workstation.
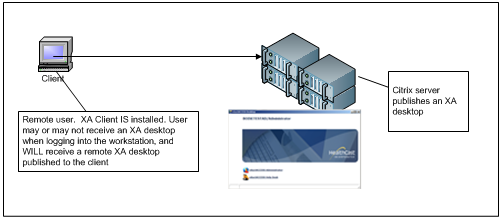
Access to this environment requires the use of the Citrix client and is not supported on the Windows Terminal Server platform.
Note
Windows 2008 Remote Desktop (Terminal Server) provides a similar feature via "Remote Apps" which allows applications to be "published" in a seamless window through the RDP client.
Note that links of this nature are not SSO enabled from the client workstation and are not supported by the XA client. It is recommended that this feature be used only on devices where XA client is NOT installed on the local (end-point) device.
Operation
The remote application operates as an isolated Windows user session.
Multiple applications may or may not share the same session.
Session management is handled by terminal server or Citrix sessions.
Session Lock and Logoff times are configured via terminal server or Citrix settings, however, they can also be controlled by ExactAccess settings.
The end user receives a single XA desktop running on the Citrix Server.
Graceful Logoff is handled by ExactAccess (WatchForLogoff.exe or AutoLogoff.exe)
Wrappers share the same session, as they are launched from the XA desktop.
There are two methods for publishing an XA desktop:
Publish only the XA desktop, and let the server handle session timeouts.
Publish the appropriate application link and let XA handle session timeouts.
In order for Citrix session timeouts to be handled properly for Graceful Logoff, it is necessary for WatchForLogoff.exe to be running in the remote session.
Create a batch file to launch the following items:
Tip
c:\program files\HealthCast\ExactAccess\watchforlogoff.exe
c:\program files\HealthCast\ExactAccess\XAUCM.exe
Publish this batch file as an application and configure the appropriate session timeouts using the Citrix or Terminal Server tools and settings.
In order for ExactAccess session timeouts to operate, it is necessary for autologoff.exe to be running in the remote session.
Create a batch file to launch the following items:
Tip
c:\program files\HealthCast\ExactAccess\autologoff.exe
c:\program files\HealthCast\ExactAccess\XAUCM.exe
Enable the following registry key:
Tip
HKEY_LOCAL_MACHINE\Software\HealthCast\ExactAccess
AutoLogoffEnabled: reg_dword = 1
Configure the appropriate lock and logoff time settings by using the Client Configuration tool on the Citrix server.
Publish this batch file as an application
Tip
If you are using a combination of Citrix/Terminal Server session timeouts and ExactAccess Timeouts, include watchforlogoff.exe in the batch file.
c:\program files\HealthCast\ExactAccess\autologoff.exe
c:\program files\HealthCast\ExactAccess\watchforlogoff.exe
c:\program files\HealthCast\ExactAccess\XAUCM.exe