Server Configuration Tool
Communications Configuration
The initial page will display the communications settings for the ExactAccess Server. Use the tabs along the top to choose which server service to configure, and the tabs along the right to choose the settings category for the server.
For initial configuration, no changes are necessary on this page, however, if there is a conflict with port assignments on the server, it is possible to change the communications ports used by the ExactAccess server. Change made to these port numbers will require similar client settings changes.
Tip
Fore more detailed information on communications, see the configuration tool page for the appropriate service: Prox Card, Remote Authentication, XA, Audit, and Deploy
Prox Card, Remote Authentication, XA, Audit, and Deploy.
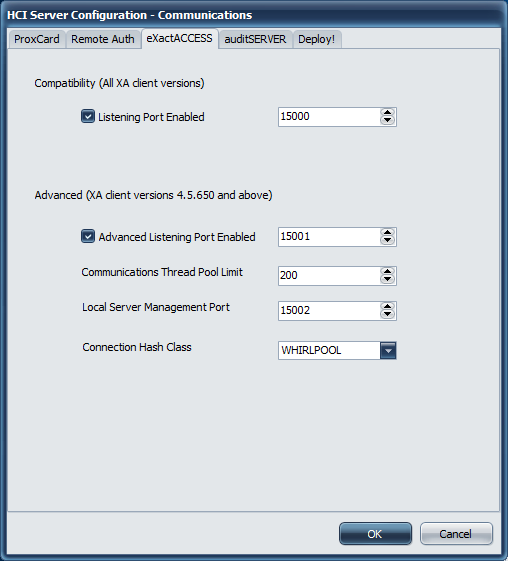 |
The Compatibility port (default 15000) allows for communications to take place using the original protocol and is compatible with all XA client version. The check box allows this port to be disabled on the server if desired. If the port is disabled, it is no longer necessary to forward that port in a load balancer, and older client versions will not be able to communicate with the server.
An advanced communications protocol is available when using an XA client version 4.5.650 or higher. This protocol is more secure, and allows for the encryption technology to be negotiated from the client.
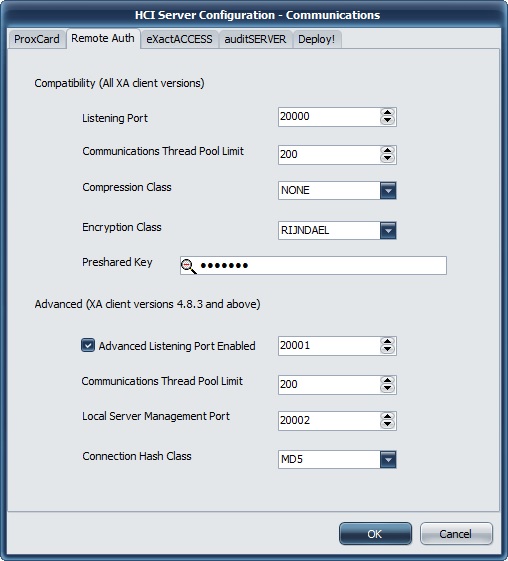
Client versions 4.5.650 through 4.5.767 support the following encryption standards:
BLOWFISH and RIJNDAEL.
Client versions 4.5.840 and above support the additional encryption standards:
BLOWFISH256, RIJNDAEL256, TWOFISH, and SERPENT.
BLOWFISH — Popular 128 bit encryption.
RIJNDAEL — 192 bit encryption using the Rijndael algorithm..
TWOFISH — AES Finalist. 128 bit encryption.
SERPENT — AES Finalist. 128 bit encryption.
BLOWFISH256 — 256 bit encryption using the Blowfish algorithm.
RIJNDAEL256 — 256 bit encryption using the Rijndael algorithm.
RIJNDAEL128 — AES 128 bit encryption using the Rijndael algorithm. Compatible with QwickACCESS
Client registry changes are necessary to enable support for the advance communications protocol.
The management port is used by the ExactAccess server monitor. This port is only used on the local server, so it is not necessary to port forward this in a load balancer.
Remote connections are not supported from the management port.
The connection Hash Class settings is used for protocol negotiation. The available options are MD5 and WHIRLPOOL. MD5 is a lightweight hash algorithm that generates 128 bit hashes, but it only recommended if the client workstations connecting to the system are slow (less than 2GHz). WHIRLPOOL is a hash algorithm that generates 512 bit hashes. The larger number of bits means it is more secure, but it also requires slightly more CPU cycles to generate. WHIRLPOOL is the recommended choice if your workstations are 2GHz or better.
The remaining tabs for each of the other services are very similar to the above, with the exception of the Remote Authentication service. This service requires that both the client and server be configured with the same values, as the protocol is not negotiated during a connection.
The preshared key is an encryption key that must be configured on both the client and the server. This is essentially a secret shared between the client and the server used to encrypt the data during communications.
 |
Database Configuration
The following server services require database configuration if the specified service is enabled.
Required: ExactAccess Server
Optional: ProxCard Server
Optional: auditSERVER
Optional: Deploy Server
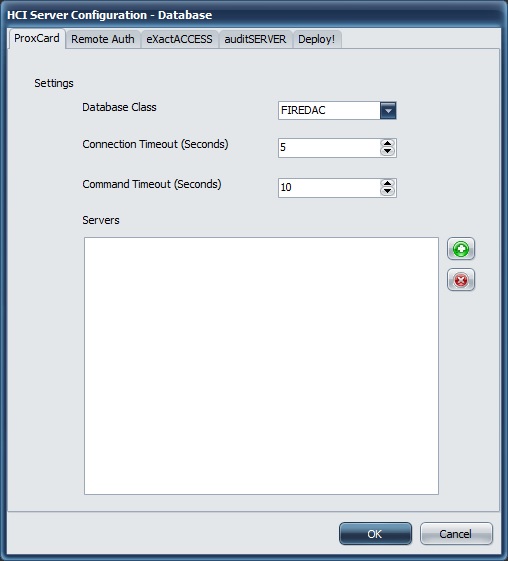
The Database Class choice is FireDAC. Select the database that has been installed on the XA server(s) to begin configuration.
The database must be the same across load balanced servers for a particular service so that database replication may be configured. It is therefore recommended that you choose a single technology, and configure all services to use the same database provider.
Tip
Fore more detailed information on database, see the configuration tool page for the appropriate service: Prox Card, XA, Audit, and Deploy.
Driver Download
Check with the Microsoft Site for newer or additional drivers for supporting the latest versions of SQL server.
To begin, click the new button ( ) to initiate the Data Link properties page. Once an appropriate database connection string has been configured, the database connection class and server name will be added to the servers list. The first server in the list will be the primary database. For load balanced (not clustered) environments, it is recommended to place the secondary server in this list as well. Double clicking on a server will allow editing of an existing connection for reconfiguration. A connection may be deleted by selecting it from the list and pressing the delete button (
) to initiate the Data Link properties page. Once an appropriate database connection string has been configured, the database connection class and server name will be added to the servers list. The first server in the list will be the primary database. For load balanced (not clustered) environments, it is recommended to place the secondary server in this list as well. Double clicking on a server will allow editing of an existing connection for reconfiguration. A connection may be deleted by selecting it from the list and pressing the delete button ( )
)
Note
To edit or update an existing entry, double click the entry in the list.
The remaining tabs for each of the other services are very similar to the above, with the exception of the Remote Authentication service. This service does not require database configuration, so no database options appear for this service.
 |
Other Configuration
The following services contain additional configuration options:
Required: ExactAccess Server
Optional: ProxCard Server
Optional: auditSERVER
Optional: Remote Authentication Server
Note
The HCIDeploy service does not contain additional configuration options beyond the communication or database settings.
Tip
Fore more detailed information on communications, see the configuration tool page for the appropriate service: Prox Card, Remote Authentication, XA, and Audit.
ExactAccess Server
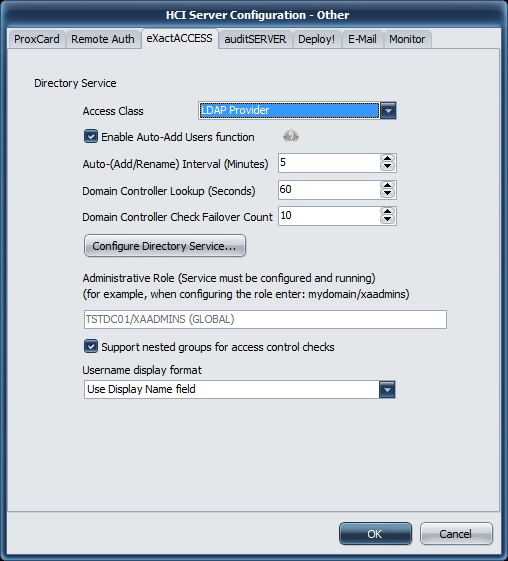
Directory service options appear in this page.
Access Class
The access class is used to determine how the ExactAccess server will communicate with the domain. The options include:
LDAP Provider — the basic LDAP provider used to request information from the domain controllers. This provider will display UNIVERSAL groups. LDAP is intended to reduce the network bandwidth required for directory communications. LDAP does not allow anonymous connections, therefore, the ExactAccess server must be configured to run under a domain account that has permissions to read the directory.
LDAP Global Catalog Provider — similar to the LDAP provider (it has the same limitations), this provider uses a Global Catalog Server for user and role lookups. For very large organizations with multiple domains within a forest, a global catalog is used as a cached data store of all domain "trees" within the "forest" of an Active Directory. It provides improved performance over the LDAP Provider when the domains are across WAN links. This makes it the ideal choice for multi-facility integration where each site maintains their own domain that is part of the same forest, spanning multiple locations. All domains should have two-way trusts, and replicate their user and role information into the Global Catalog so that each domain data set is available on every Global Catalog server in the forest. If a user lookup in the Global Catalog fails, a fallback lookup using standard LDAP will be performed against the user account domain server(s). Note that the Global Catalog will only contain UNIVERSAL group membership information for accounts that are not part of the domain the GC is hosted on. This means that only UNIVERSAL groups may be used when assigning access permissions with this multi-site configuration.
 |
