Standard Mode Configuration
Features
Standard mode provides the familiar Windows user experience to end users with explicit sessions, coupled with the convenience of proximity card login. ExactAccess provides session management features to enhance workflow for shared or dedicated workstations.
Supported Proximity Card Readers
(available through HealthCast)
Card Type | RFIdeas Reader Models 1 | HID Global/OmniKey | |||||
|---|---|---|---|---|---|---|---|
HID® cards |
|
| |||||
iCLASS® cards |
|
| |||||
Indala® cards |
| ||||||
MiFARE® cards |
|
1 Reader models cannot be mixed in the same environment.
2 Card serial number (CSN) do not support Parity Checking, Facility ID filtering, or Badge ID range checking features provided by ExactAccess.
Warning
Card readers that only read the card serial number (CSN) cannot be configured with these advanced features such as Parity Checking, Facility ID filtering, and Badge ID range checking.
Note
Card readers supporting card serial number (CSN) typically read 64-bit serial number values.
3 Reader must be pre-configured for compatibility with card type and data type, as the reader supports dual band communications. Only a single band can be utilized at a time 1.
4 Parity Checking, Facility ID filtering, or Badge ID range checking features are not available with this reader model.
Configuration - Enabling PIN
See enabling PIN below for configuration steps.
Configuration
Log-in as a Local Administrator to the workstation you would like to make changes on. The Client Configuration Tool will only run under an account with Local Administrator privileges.
Navigate to the Windows® Start menu> All Programs > HealthCast > ExactAccess > Utilities > Configuration > Client Configuration.
Click the General tab
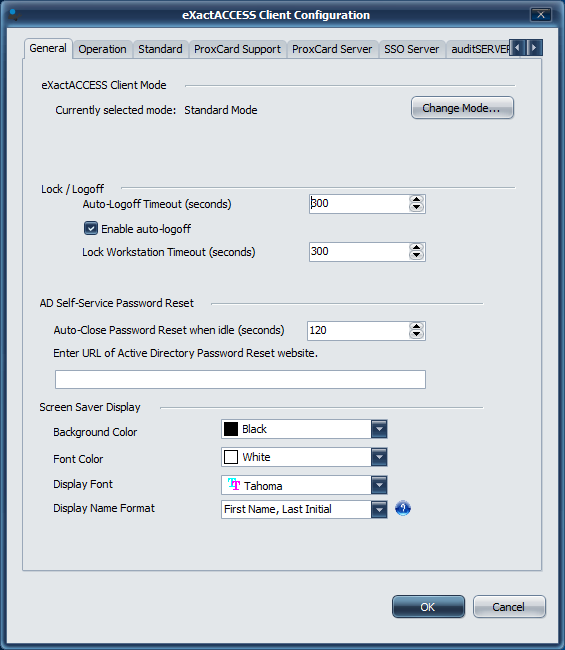
On this page, you can choose the Lock and Logoff timeouts. For an explanation of these options, see the Lock settings below.
In addition, you can configure a URL for a web based Password Reset to help users fix account lock out issues.
Click the Operation tab to show the type of configuration
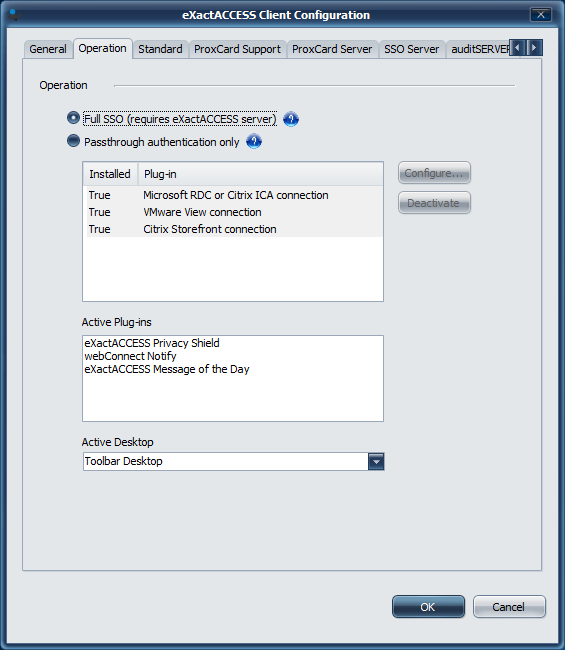
Ensure that Full SSO option is enabled so that users can use local resources of this device
Click the Standard tab to configure additional options
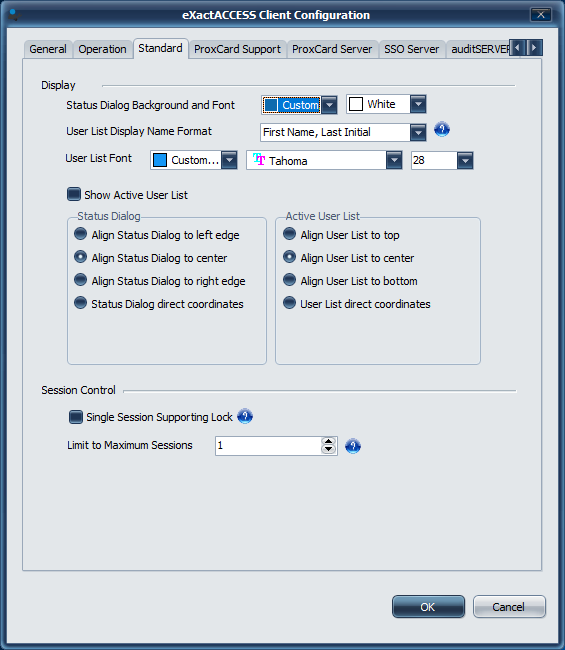
On this page, you can configure the presentation of the dialogs shown on the Windows Secured Desktop screen. To enable the active session list display, ensure the "Show Active User List" ** setting is checked (It can be enabled by ensuring Limit active logins to a single session is checked). If you want to remove limiting the number of sessions on Windows workstations, ensure the "Limit active logins to a single session" *** setting is unchecked.
Info
** The Active User List will only show the session in which ExactAccess has an authenticated user (XAUCM.exe is running), and Limit sessions is ON.
** If the GPO "don't show last user name" is enabled, navigation from the Active User List will only present the tile that requires the user to enter both their username and their password instead of navigating to the tile with the username preset.
*** Limit active logins to a single session will only close ExactAccess sessions as displayed by the Active User List. If a session is created, and ExactAccess is closed within the session, a new user log-in will not close this session, and the session will not display in the Active User List.
This facilitates administrative logins remaining open (if the administrative login happens after a user session is already present, that user will be logged off).
Tip
If Single Session Supporting Lock is enabled, then proximity card tap-over is disabled. This allows for true single user workstation configurations that may be adversely affected by the Microsoft Windows multiple session feature disconnecting the session from the display devices. In this scenario, the workstation is locked, and only the returning user or an administrator may log into the workstation.
Info
Limiting active sessions to 1 is not the same as Single Session support, though they are similar in the number of active sessions allowed on the workstation.
In the case of Limiting the number of active sessions, users are allowed to tap-over (and potentially preserve) other user sessions based on the current session count on the system and the setting specified in "Limit to Maximum Sessions". The session is disconnected and the user is presented with the Windows Login screen when they tap out or select Lock from the ExactAccess Desktop.
Single session does not support tap-over, and the workstation is actually sent to the Windows Session Lock screen when a user taps out or select Lock from the ExactAccess Desktop.
To enable PIN support, select the ProxCard Support tab
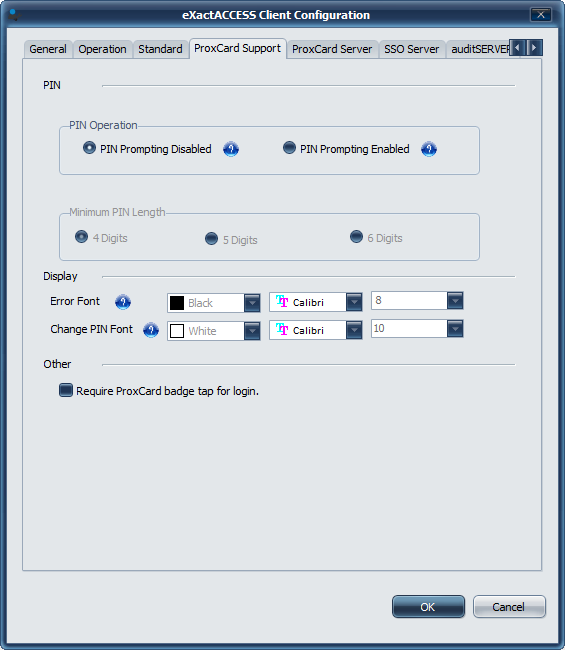
Here, you can select to enable PIN prompting. Optionally, select the length of PIN required for enrollment on this workstation.
You can also select the option to require a prox card be tapped to initiate login. A user then must tap a badge in order to log into the workstation.
Note
Requiring prox cards for login disables other methods of login for Windows sessions, meaning that the standard Windows login tiles are not select-able.
Info
The Error Font, and Change PIN font settings on this page do not apply to standard mode. These settings apply to kiosk mode display only.
Configure other options that are appropriate for your environment and click OK to finish.
If you have questions about which Standard mode options are right for you (user list display, session limiting, etc.) please contact your HealthCast project manager for help. A system reboot may be required. If you are prompted, please reboot your system.
Info
If you are not prompted to reboot, it may still be necessary to log off the current Windows session for settings to take effect.
Changing the name format of the logged in user
(displays on the Active User List, but does not affect the user login tiles provided by Windows)
Log-in as a Local Administrator to the workstation you would like to make changes on. The Client Configuration Tool will only run under an account with Local Administrator privileges.
Navigate to the Windows® Start menu> All Programs > HealthCast > ExactAccess > Utilities > Configuration > Client Configuration.
Click the General tab to show the customization options available. (The option also appears on the Kiosk Mode tab)
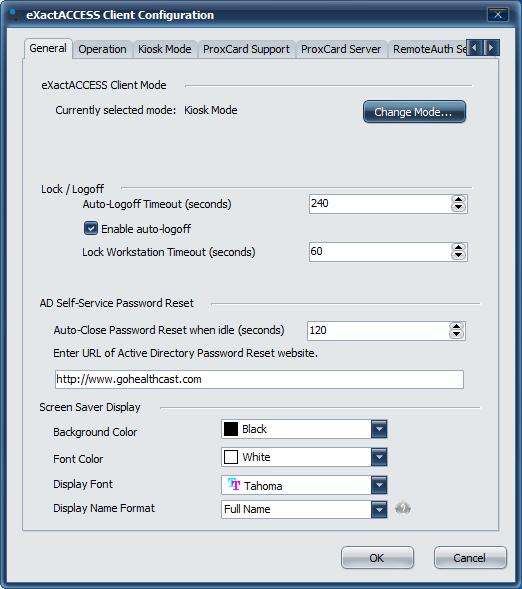
Using the drop-down arrows of Display Name Format (at the bottom of the dialog), select the options that are appropriate for your environment and click OK to finish.
The new settings should now show when your XA screen saver, privacy shield, or Active User List is displayed. A reboot may be necessary in some environments. If prompted, please reboot your workstation.
Choose the appropriate Username display format by using the following server-side instructions for LDAP Privacy Shield Settings.
Tip
If you are connecting this client version to a server older than 4.8.3, the LDAP provider must be configured for the XA server instead of the WinNT provider in order to use the First Name, Last Name fields, instead of Display Name.
Note
If you are using Kiosk Mode Passthrough Authentication only, the following Username Settings are available:
3. Directory Service Name
7. In use only
8. No username display.
Registry Settings
HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess
KMLockDisplayMode: reg_dword = 0
0. Full Name
1. Last Name only
2. First Name only
3. Directory Service Name
4. Initials Only
5. First Name, Last Initial
6. First Name Initial, Last Name
7. System In Use
8. No user name (can also be set on the privacy shield independently)
Bitcount and Parity Checking
Caution
Not all badge readers or IDs will function with this feature. See System requirements for details.
These instructions are intended for XA solutions utilizing badge tap functionality. You must have badges and compatible badge readers in your environment in order to successfully monitor the bit count.
You can set the bit count in the registry to reflect the number of bits in your proximity card identification data. This is advisable if you wish to minimize the possibility that badge reads will be in error.
This is a custom security measure that will minimize the possibility that bad badge reads will cause unwanted outcomes in your environment.
Once the bit count has been set to a specific value, all cards with values that are not specified will be rejected and will not be able to create or connect to a user session. They will NOT be allowed.
Configure Bit Count Monitoring in the Registry
Go to Start >Run >Regedit.
In the Registry Editor, locate the ValidBitCount value located at:
HKLM\Software\HealthCast\ProxCardClient The ValidBitcount value may not be present. You may need to add this value as a string in the ProxCardClient folder located in the directory path above.
Modify the value to indicate the allowed bit count(s): 26, 35, or 37.
Multiple values may be used. Please put a comma between each value to separate them. We do support values other than 26, 35, or 37. If you have a bit count value that is not one of the standards listed above, please follow the instructions in the next section, Creating a New Bit Count Value.
Example: If the bitcount for your card type is 26, your final registry setting will look like this:
ValidBitCount:reg_sz="26"
If you have multiple cards with varying bit counts, your final registry setting may look similar to this:
ValidBitCount:reg_sz="26,35,37"
Creating a New Bit Count Value
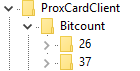
In the Registry Editor, locate the Bitcount key located at: HKLM\Software\HealthCast\ProxCardClient\Bitcount.
Create a new key within the Bitcount key. Use the number of your badges bits as the name of the new key.
Because there are other configuration options based on the bit count of your badges, you will need to create some additional keys.
In the newly created key (this key should be named with the number of bit counts contained in your badges), you must create another key. Please name this key Facility.
Example
If the bitcount for your card type is 36, you would create the following registry structure:
HKLM\Software\HealthCast\ProxCardClient\Bitcount\36\facility
You would then modify the ValidBitcount value found in in HKLM\Software\HealthCast\ProxCardClient, adding your value of 36 by either replacing all other data in this value, or by appending ",36" to the end of the current list specified within the value.
The final registry setting would be similar to this:
ValidBitCount:reg_sz="36"
or
ValidBitCount:reg_sz="26,35,37,36"
Parity Settings
This is a custom setting that will minimize the possibility that bad badge reads will cause unwanted outcomes in your environment.
Parity stripping is turned OFF by default. The default setting ( 0 ) allows your system to collect data regarding the parity bits contained in your proximity badge identification data. Leave this setting as is if you are installing XA Client in your environment for the first time. It will allow for advanced troubleshooting and quicker resolution to proximity badge issues if they occur.
Changing this setting will strip the desired number of bits from your proximity badge identification data. This changes the number of bits that is stored in the ProxCard Server database to reflect the identification data minus the number designated to be stripped.
Upgrade
Change this setting if you are upgrading and have a ProxCard Server database that is already populated with user data from workstations that had this setting ON (1).
Users will need to re-enroll their badges when this setting is changed.
Configure Parity Stripping
Go to Start >Run >Regedit.
In the Registry Editor, locate the ParityStripcountLeading and ParityStripCoundTrailing values located at:
HKLM\Software\HealthCast\ProxCardClient
Modify them to indicate the value of 1.
One bit stripped from the front and back of the data sequence is the most common scenario. If you feel your parity settings may be different, please contact your HealthCast Project Manager for assistance.
If you use the parity stripping setting, please ensure that your final bit count is 24 bits or more. A bit count of less than 24 bits will make badges unusable.
Facility Code Validation
This is a custom setting that functions as a way to limit access to workstations based on the facility portion of a user's badge code. Validating facility code will minimize the possibility that bad badge reads will cause unwanted outcomes in your environment. This includes prohibiting the use of unauthorized proxcards.
Configuring the facility code validation feature requires adding new keys and values to the workstation's registry. This can be done via a transform or batch file during install or upgrade, or post-install/upgrade using the Registry Editor.
Instructions for configuring the facility validation feature will differ depending on your method of deployment, if you are installing XA for the first time, and if you are configuring your environment for parity stripping. Please contact your HealthCast representative before configuring facility validation if your scenario differs from those described below.
Set the facility mask
Go to Start >Run >Regedit.
Verify that the correct number of bits is specified in the ValidBitCount value located in the registry under: HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ProxCardClient
Select one of the sub-keys under the BitCount key which reflect the bit count of the badge. The options are 26 and 37 bits.
Tip
Please ensure that your final bit count is 24 bits or more. A bit count of less than 24 bits will make badges unusable.
In the sub-key under Bitcount which reflects the number of bits in your badge (our defaults are 26, 35, and 37 you may have created another key with the appropriate number for your environment) create the following value:
FacilityMask: reg_binary
Enter the appropriate hexadecimal value of your facility mask in the FacilityMask value.
This should be set in hexadecimal.
Example
Example: If you have a bit count of 36, you would create the following keys in the registry:
HKLM\Software\HealthCast\ProxCardClient\Bitcount\36
Under the 36 key, you would create the following value: Facility Mask as a binary value.
FacilityMask:reg_binary=00 00 00 01 ff e0 00 00
Continue by setting the accepted facility codes.
Set the accepted facility codes
Have the appropriate facility codes ready before continuing. The facility codes entered in this section will be the only allowable codes once this configuration is finished.
In the Facility key, create a new reg_dword value.
Name the value 1..
Right-click the new value and select Modify.
Select the appropriate Base category.
Choose Decimal if your facility code was provided by the manufacturer of your card and it is in decimal notation. Choose Hexadecimal if you have calculated the facility mask in hexadecimal notation.
In the Edit DWORD Value box enter one of the facility codes in the Value data box.
Verify that the information in the box is correct, and select OK.
Repeat these steps for each facility code that you would like to authorize. Name the values sequentially.
Required
Warning
If you already have a proxcard database in place and are using parity stripping, then it is critical that your bit count settings, and other badge related registry settings, are correct.
First, verify the state of your parity settings.
If your settings indicate that you are stripping bits (leading or trailing), then you must adjust your bit count to match the number of bits present AFTER parity bits have been removed.
Example: If you are removing 1 leading parity bit and 1 trailing parity bit and you have 26 bit cards, you would calculate the final bit count as 24. If you have 35 bit cards and are stripping 2 leading bits and 1 trailing bit you would calculate the final bit count as 32.
Set the correct bit count in the registry.
You may need to create new keys and sub-keys that reflect the bit count in your environment.
Recalculate your facility mask using the final bit count derived from the bits remaining after parity stripping.
Follow the directions above in the fresh installation/non-parity stripping section to configure the facility code validation.
Registry Settings
Server Connection Properties
Parameter Name | Applicable Modes | Registry Keys Affected | Value | Setting Description |
|---|---|---|---|---|
XA_SRV | ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess\Servers\INDY 0000: reg_sz | Valid Server NETBIOS or FQDN Name or IP address | Primary XA (SSO) server name |
XA_AUDIT_SRV | ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\AuditServerClient\Connection\INDY 0000: reg_sz | Valid Server NETBIOS or FQDN Name or IP address | auditSERVER name |
XA_PRX_SRV | ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ProxCardClient\Indy 0000: reg_sz | Valid Server NETBIOS or FQDN Name or IP address | Prox Card Server Name |
X_D_SRV | ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\HCIDeployClient\Indy 0000: reg_sz | Valid Server NETBIOS or FQDN Name or IP address | HCIDeploy server name |
X_RA_SRV | KM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\HCCitrixSessionDirectory\INDY 0000: reg_sz | Valid Server NETBIOS or FQDN Name or IP address | Remote Authentication Server name |
X_PREF_IPV4 | ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ProxCardClient PreferIPv4: reg_dword HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess PreferIPv4: reg_dword HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\AuditServerClient PreferIPv4: reg_dword HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\HCCitrixSessionDirectory PreferIPv4: reg_dword HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\HCIDeployClient PreferIPv4: reg_dword | 1 | Indicates that any TCP/IP communication prefers to use IPv4 when IPv6 is installed and available This setting will be ignored if the *_SRV setting(s) listed above contain a direct IPv6 address. |
SSO Client Settings
Parameter Name | Applicable Modes | Registry Keys Affected | Value | Setting Description |
|---|---|---|---|---|
X_SP | ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess\Servers\INDY Port: reg_dword | 15001 | Communications port for XA (SSO) server |
ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess\Servers\INDY EnabledServerIDs: reg_sz | 0000 | Enabled Servers List. Comma delimited list of server identifiers 0000,0001,0002, etc. | |
XA_EC | ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess\SocketTransport\Indy Encryption: reg_sz | RIJNDAEL | Encryption Class: RIJNDAEL, RIJNDAEL128, RIJNDAEL256, BLOWFISH, BLOWFISH256, TWOFISH, SERPENT |
XA_CC | ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess\SocketTransport\Indy Compression: reg_sz | VCLZIP | Compression Class: NONE, VCLZIP |
Proxcard Client Settings
Parameter Name | Applicable Modes | Registry Keys Affected | Value | Setting Description |
|---|---|---|---|---|
XA_PRX_SRV_PRT | SUM,KM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ProxCardClient\Indy Port: reg_dword | 30000 | Communications port for Proxcard Server |
ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ProxCardClient\Indy EnabledServerIDs: reg_sz | 0000 | Enabled Servers List. Comma delimited list of server identifiers 0000,0001,0002, etc. | |
SUM,KM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess\SocketTransport\Indy Encryption: reg_sz | RIJNDAEL | Encryption Class: RIJNDAEL, RIJNDAEL128, RIJNDAEL256, BLOWFISH, BLOWFISH256, TWOFISH, SERPENT | |
SUM,KM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess\SocketTransport\Indy Compression: reg_sz | VCLZIP | Compression Class: NONE, VCLZIP | |
X_PROX_RT | SUM,KM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ProxCardClient ReaderType: reg_sz | USB | ProxCard ReaderType USB - RFIdeas USB device support RFVC - RFIdeas Linux -> Citrix session support RFSerial - RFIdeas Reader Serial device support SCARD - OMNIKEY Reader support |
X_PSE | SUM,KM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ProxCardClient\PIN PinPromptInMinutes: red_dword | 4294967295 | Specify enabling PIN Support. Users will be prompted to validate with pin: Set this to enabled (4294967295) or disabled (0) |
X_PIN_LEN | SUM,KM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ProxCardClient\PIN MinPinLength: reg_dword | 4 | Specify the minimum PIN length a user must use when enrolling a PIN: 4, 5, or 6 |
X_ALLOW_PIN | SUM,KM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ProxCardClient\PIN AllowPinEnrollment: reg_dword | 1 | Set this to enable (1) or disable (0) PIN Self enrollment. |
X_PSCL | SUM,KM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ProxCardClient ParityStripCountLeading: reg_dword | 0 | Parity Strip Count Leading bits |
X_PSCT | SUM,KM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ProxCardClient ParityStripCountTrailing: reg_dword | 0 | Parity Strip Count Trailing bits |
X_BBS | SUM,KM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ProxCardClient BlankBadgeScan: reg_dword | 1 | Blank Badge Scanning allowed - if this setting is disabled, enrollment of unassigned cards is disabled. |
X_HPI | SUM,KM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ProxCardClient HardwarePollInterval: reg_dword | 500 | Hardware polling interval in milliseconds |
X_TOUT | SUM,KM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ProxCardClient SupportTapoutUpdateTime: reg_dword | 1 | Rolling password save enabled |
X_PSWT | SUM,KM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ProxCardClient ServiceStartupConnectionWaitTimeout: reg_dword | 30 | Service Startup Connection Wait Timeout in seconds |
X_VBC | SUM,KM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ProxCardClient ValidBitCount: reg_sz | Valid Bit Count comma delimited list | |
X_PIBCM | SUM,KM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ProxCardClient InvalidBitCountMessage: reg_sz | Message to display to user when their card has an invalid bit count | |
X_PIFM | SUM,KM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ProxCardClient InvalidFacilityMessage: reg_sz | Message to display to user when their card has an invalid facility code | |
X_PIPM | SUM,KM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ProxCardClient InvalidParityMessage: reg_sz | Message to display to user when their card has an invalid parity calculation | |
X_PIRM | SUM,KM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ProxCardClient InvalidRangeMessage: reg_sz | Message to display to user when their card has an ID that is not in a valid range | |
X_PSEDM | KM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ProxCardClient SelfEnrollmentDisabledMessage: reg_sz | Message to display to user when prox card self enrollment has been disabled | |
X_PSDM | SUM,KM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ProxCardClient ServerDownMessage: reg_sz | Message to display to the user when the server cannot be contacted | |
X_PIN_AT | SUM,KM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ProxCardClient PIN_Auth_Title: reg_sz | AUTHENTICATION | Title of message to prompt user for PIN Authentication |
X_PIN_ET | SUM,KM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ProxCardClient PIN_Enroll_Title: reg_sz | ENROLLMENT | Title of message to prompt user for PIN Enrollment |
X_CPT | SUM,KM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ProxCardClient PIN_Change_Message: reg_sz | Change my PIN | Message to prompt user for manually changing their PIN |
X_BMML | SUM,KM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ProxCardClient BadgeMsg_ManualLogin: reg_sz | Enter username and password | Message to prompt user for manual login when prox reader is not attached |
X_BMUA | SUM,KM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ProxCardClient BadgeMsg_UnAuthenticated: reg_sz | Enter your password | Message to prompt user their badge is not authenticated and a password is required |
X_BMUR | SUM,KM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ProxCardClient BadgeMsg_Unregistered: reg_sz | Enter username and password to register badge. | Message to prompt the user for badge enrollment (the card is not registered) |
X_PX_RB | SUM,KM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ProxCardClient CardRequiredForLogin: reg_dword | 0 | Require Proxcard for Login enabled(1) or disabled(0) |
HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ProxCardClient HWGConfig: reg_sz | The full path and filename to an HWG+ formatted configuration file that will be used to configure the proximity card reader device. WarningSetting this file path overrides all other prox card device configuration settings as specified in the registry, as well as those that are built into the product. This includes Parity Strip count, Reader Beep, MessageValidForMS, and potentially ValidBitCount settings. Use caution when using this method to configure devices, and ensure proper operation before distribution. | |||
X_PSWT | HKEY_LOCAL_MACHINE\Software\HealthCast\ProxCardClient ServcieStartupConnectionWaitTimeout: reg_dword | 30 | This setting indicates how long to wait during a startup phase to ignore server/network availability errors before reporting a problem to the HealthCast client. | |
HKEY_LOCAL_MACHINE\Software\HealthCast\ProxCardClient ReaderBeepEnabled: reg_dword | Indicates if using a RFIdeas reader model that includes an internal speaker, that tapping a badge the reader will beep indicating the badge was read. | |||
ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ProxCardClient ConnectionTimeout: reg_dword | 1 | The time in seconds that the client will attempt to connect to the all of the configured servers before returning an error to the client for a connection failure. | |
SUM,KM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ProxCardClient BeepSoundFile: reg_sz | <install folder path>\beep2.wav | The default WAV file that will play when a card is tapped, and the setting to play beep sound is enabled | |
X_BEEP | SUM,KM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ProxCardClient BeepSoundPlayOnBadgeTap: reg_dword | 0 | Beep sound is enabled to play when set to 1, disabled when set to 0 |
Audit Client Settings
Parameter Name | Applicable Modes | Registry Keys Affected | Value | Setting Description |
|---|---|---|---|---|
ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\AuditServerClient\Connection\INDY SocketPort: reg_dword | 25000 | Communications port for auditSERVER | |
ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\AuditServerClient\Connection\INDY EnabledServerIDs: reg_sz | 0000 | Enabled Servers List. Comma delimited list of server identifiers 0000,0001,0002, etc. | |
ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\AuditServerClient\Connection\INDY EncryptionClass: reg_sz | NONE | Encryption Class: RIJNDAEL, RIJNDAEL128, RIJNDAEL256, BLOWFISH, BLOWFISH256, TWOFISH, SERPENT | |
ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\AuditServerClient\Connection\INDY CompressionClass: reg_sz | VCLZIP | Compression Class: NONE, VCLZIP |
HCIDeploy Client Settings
Parameter Name | Applicable Modes | Registry Keys Affected | Value | Setting Description |
|---|---|---|---|---|
X_D_PORT | ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\HCIDeployClient\Indy Port: reg_dword | 26000 | Communications port for HCIDeploy |
ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\HCIDeployClient\Indy EnabledServerIDs: reg_sz | Enabled Servers List. Comma delimited list of server identifiers 0000,0001,0002, etc. | ||
X_D_EC | ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\HCIDeployClient\Indy EncryptionClass: reg_sz | RIJNDAEL | Encryption Class: RIJNDAEL, RIJNDAEL128, RIJNDAEL256, BLOWFISH, BLOWFISH256, TWOFISH, SERPENT |
X_D_CC | ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\HCIDeployClient\Indy CompressionClass: reg_sz | VCLZIP | Compression Class: NONE, VCLZIP |
X_D_PORT_CRM | ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\HCIDeployClient\Indy ClientPort: reg_dword | 26100 | Communications port for HCIDeploy remote management |
X_D_GRPS | ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\HCIDeployClient DefaultGroups: reg_sz | Default Locations the workstation should be registered in. (When the service starts, it will register these location names, then remove the setting) | |
X_D_RM | ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\HCIDeployClient\Indy EnableRemoteManagement: reg_dword | 1 | Enable(1) or Disabled(0) management port. If this setting is disabled, the HCIDeploy Console will not be able to display the deployed package state on the workstation |
X_D_HID | ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\HCIDeployClient\Indy ConfiguredHashID: reg_sz | {A439AF92-98CD-4C20-83AC-5FD12308F51A} | Indicates the communications hash ID the remote management listening port requires for encryption handshake: MD5 (128 bit) GUID: {A439AF92-98CD-4C20-83AC-5FD12308F51A} WHIRLPOOL (512 bit) GUID: {C86DDD9B-09B2-4360-878B-F5D3B6997CDE} |
X_D_SCH | ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\HCIDeployClient\Schedule Schedule: reg_sz | Schedule information string indicates how often the client will check in with the server to determine if a package update or uninstall is needed on the workstation | |
ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\HCIDeployClient\Indy ConnectionTimeout: reg_dword | 1 | The time in seconds that the client will attempt to connect to the all of the configured servers before returning an error to the client for a connection failure. |
Miscellaneous Settings
Parameter Name | Applicable Modes | Registry Keys Affected | Value | Setting Description |
|---|---|---|---|---|
XA_ALE | ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess AutoLogoffEnabled: reg_dword | 1 | Enables (1) or Disables (0) idle session logoff. Logoff only occurs after the session has locked. |
X_KM_AL_TIME | ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess LogoffTimeLimit: reg_dword | 600 | The number of seconds the session can be idle (locked) before the session will be logged off. |
X_KM_LTL | ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess LockTimeLimit: reg_dword | 300 | The number of seconds a session can be idle before the session is automatically locked |
X_PRA | SUM,KM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\PasswordReset URL: reg_sz | Password Reset URL to a web site than allows a user to reset their domain password (such as ADPWR) | |
X_ACT | SUM,KM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\PasswordReset AutoCancelTime: reg_dword | 120 | The auto cancel time for inactivity of the password reset web display in seconds. |
ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess ShowXAStatusMessages: reg_dword | 1 | When Enabled (1) Allows XAUCM to display the status message during startup, show desktop, and shutdown. These status messages will not be shown when Disabled (0) | |
ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess SkipLoadingAppList: reg_dword | When Enabled (1) Indicates that XA should not load the application list during login to improve performance. When Disabled (0), XA will load the users application list from the server. TipThis setting is required to be Disabled (0) if the user will launch SnapApp enabled applications (either Windows or Web) on the system where the setting is set. Also, if the ExactAccess Desktop will be displaying applications on the workstation, this setting must be Disabled (0) so the users authorized applications will be loaded for presentation. Not all workstations require this setting to be disabled - for instance, in a Published Application scenario, this setting can be enabled on the RSM server if the user will launch WebSSO or Windows SnapAPP applications on their local workstation and use published connectors for applications on the RSM server. This setting can also be Enabled (1) when using the Kiosk Mode Passthrough configuration, as the desktop presentation will be handled by an RSM or VDI desktop (remote session), so the local workstation does not need to retrieve the application list. | ||
ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess BeepBeforeLockEnabled: reg_dword | Enables (1) or Disables (0) a system beep during the about to lock countdown | ||
ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess LockBeepIntervalInSeconds: reg_dword | This value is how many seconds occur between each beep during the countdown before lock. | ||
ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess LockBeepStartTimeInSeconds: reg_dword | This value is how many seconds before lock does the beep notice start to occur. It also indicates when the visual status will indicate the system is about to lock. | ||
ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess LockBeepIndex: reg_dword | 32 | May be one of the following values 0 - play sound associated with Default Beep sound in the Sound Scheme 16 - play sound associated with Critical Stop sound in the Sound Scheme 32 - play sound associated with Question sound in the Sound Scheme 48 - play sound associated with Exclamation sound in the Sound Scheme 64 - play sound associated with Asterisk sound in the Sound Scheme 4294967295 - use PC Speaker beep instead of scheme sound TipNote that the user may not have a .WAV file associated with the Sound Scheme values listed. Verify with the Sound Scheme that each of the items identified is associated with a .WAV file. These values can be found under: HKEY_CURRENT_USER \AppEvents \Schemes \Apps \<Type> \.Current -- (Default) Where <Type> is one of the following values: .Default, SystemHand, SystemQuestion, SystemExclamation, SystemAsterisk | |
X_LDM | ALL | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess KMLockDisplayMode: reg_dword | 5 | Change how the user name is displayed in the Active User List, Privacy Shield, and the XA Desktop 0 - Full Name* 1 - Last Name only 2 - First Name Only 3 - Directory Service Name ** 4 - Initials Only 5 - First Name, Last Initial 6 - First Initial, Last Name 7 - "In use" only ** 8 - No user name display ** Warning* Full Name is the First + Last, or Display Name field, depending on how the server is configured. Warning** In Passthrough configuration, only values 3,7,8 are valid. ** Optionally, in Kiosk Mode, The user name can be removed from the privacy shield with the PSLoginNameVisible setting (allowing the name to remain showing on the XA Desktop) |
ALL | HKLM\Software\HealthCast\ExactAccess\Override LogoffOnDesktopClose: reg_dword | Enables (1) or Disables (0) initiating logoff if the user closes the Application Desktop (not valid for Toolbar Desktop) | ||
ALL | HKLM\Software\HealthCast\ExactAccess\Override ShowDesktopOnLogoffCancel: reg_dword | Enables (1) or Disables (0) initiating re-launching the XA Application Desktop (not valid for Toolbar Desktop) if the user cancels logoff | ||
ALL | HKLM\Software\HealthCast\ExactAccess\Display DesktopStyle: reg_sz | hcgreen.vsf | The visual style file applied to change the look and feel of the XA Toolbar Desktop (not valid for Application Desktop). | |
XA_DSK_CLASS | ALL | HKLM\Software\HealthCast\ExactAccess\XAServerManager Desktop: reg_sz | AppDesktop.clsAppDesktop | AppDesktop.clsAppDesktop: also referred to as Application Desktop, launches an application window similar to a web page that lists the user's SSO enabled applications as well as "lock" and "logoff" buttons. NoDesk.clsNoDesk: also referred to a No Desktop, does not launch an XA Desktop when XA is started. xatbdesk.clsxatbdesk: also referred to as Toolbar Desktop allows for the XA Menu to appear as a popup/context menu from the XA Taskbar icon. Additionally, a secondary application can be launched that looks and acts like the standard Windows task/start bar in that it will display favorite applications and has a start button to display a popup menu of applications with a work space similar to Windows 10. HCCitrixDesk.clsDesktop is a specialized desktop presentation used when the same Citrix server publishes a full Windows desktop and the user should see an XA menu of SSO enabled applications. The same Citrix server may also be used to publish xa directly but have the nodesktop option so an xa desktop does not appear. RequiredWhen using the XATBDesk.clsXATBDesk class, it is necessary that the DESKTOP_SERVER.XML be registered with the XA server before it will function. See Registering application XML files in the ExactAccess Administrator. |
All | HKLM\Software\HealthCast\ExactAccess\XAServerManager ClientDSProgID | NoteThis setting must be manually updated after an installation on RSM to use the virtual channel class to retrieve the current XA user from the end point device. Using the Client Configuration tool may reset this value when saving settings. WarningThis setting may not be set during the install or with a transform. | Class that determines where the user identification is retrieved from. NTClientDSUser.clsNTClientDSUser (SUM,RSM,VDI) hciVCCred.clshciVCCred (RSM ONLY) NTKMDSUser.clsNTKMDSUser (KIOSK ONLY) | |
X_ALA_CHK | ALL | HKLM\Software\HealthCast\ExactAccess\AutoLaunch CheckAccess: reg_dword | 0 | This setting determines whether an access check should be performed before the application is auto-launched. If the value is set to zero (0), the application will be launched and is not required to be registered in XA. The user logging in does not have to be granted access to launch the application. If the value is set to one (1), the application must be registered in XA and the user must belong to a role that has been granted access to the application. |
X_ALA_PATH | ALL | HKLM\Software\HealthCast\ExactAccess\AutoLaunch Launch: reg_sz |
Standard Mode Only Miscellaneous Settings
Parameter Name | Applicable Modes | Registry Keys Affected | Value | Setting Description |
|---|---|---|---|---|
X_AULV | SUM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess\QAW\Settings ActiveUserListVisible: reg_dword | 0 | Enables (1) or Disables (0) the Standard Mode Active User List display that shows the active ExactAccess Sessions/Users on the workstation |
X_LS | SUM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess\QAW\Settings LimitSessions: reg_dword | 1 | Limit sessions to a single session with tap-over supported 0=session limit disabled (unlimited number allowed) 1 or more=session limit enabled with define number allowed |
X_DTO | SUM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess\QAW\Settings SingleUserOnly: reg_dword | 0 | Enalbles (1) or Diables (0) Single User only operation. Tap-Over is disabled when this setting is enabled. The session locks rather than disconnecting when this setting is enabled. |
SUM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess\QAW\Settings QAW.PasswordResetEnabled: reg_dword | Enables (1) or Disables (0) Password reset link on the login tile. Requires the password reset URL also be configured. | ||
X_QSA | SUM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess\QAW\Settings QAW.STATUS_ALIGNMENT: reg_dword | 1 | Proximity card dialog alignment 0=Left 1=Center 2=Right 3=Absolute Position (use X_QSX, X_QSY to specify position) |
X_QSBC | SUM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess\QAW\Settings QAW.STATUS_BACK_COLOR: reg_dword | 11430670 (AE6B0E) — blue | Credential Provider Dialog Background Color Color is specified in the following format: NBGR (none,blue,green,red values from left to right 00, BB, GG, RR) |
X_QSFC | SUM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess\QAW\Settings QAW.STATUS_FONT_COLOR: reg_dword | 16777215 (FFFFFF) — white | Credential Provider Dialog Font Color Color is specified in the following format: NBGR (none,blue,green,red values from left to right 00, BB, GG, RR) |
X_QSX | SUM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess\QAW\Settings QAW.STATUS_XPOS: reg_dword | 0 | Status Dialog Absolute X (horizontal) position |
X_QSY | SUM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess\QAW\Settings QAW.STATUS_YPOS: reg_dword | 0 | Status Dialog Absolute Y (vertical) position |
X_QULF | SUM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess\QAW\Settings QAW.USER_LIST_FONT_NAME: reg_sz | Tahoma | Active User List Font Name |
X_QULA | SUM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess\QAW\Settings QAW.USERLIST_ALIGNMENT: reg_dword | 1 | Active User List Dialog Alignment 0=Top 1=Center 2=Bottom 3=Absolute Position (use X_QULX, X_QULY to specify position) |
X_QULFC | SUM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess\QAW\Settings QAW.USERLIST_FONT_COLOR: reg_sz | 16094997 (F59715) — blue | Active User List Item Font Color Color is specified in the following format: NBGR (none,blue,green,red values from left to right 00, BB, GG, RR) |
X_QULFS | SUM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess\QAW\Settings QAW.USERLIST_FONT_SIZE: reg_sz | 28 (1C) | Active User List Item Font Size |
X_QULX | SUM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess\QAW\Settings QAW.USERLIST_XPOS: reg_sz | 0 | Active User List Dialog Absolute X (horizontal) position |
X_QULY | SUM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess\QAW\Settings QAW.USERLIST_YPOS: reg_sz | 0 | Active User List Dialog Absolute Y (verticle) position |
X_QASE | SUM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess\QAW\Settings QAW.MSG.SELFENROLLDISABLED: reg_dword | 0 | Disables (1) or Enables (0) Prox Card Self Enrollment for Standard Mode |
SUM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess\QAW\Settings QAW.TRANSPARENT_BACKGROUND: reg_dword | 1 | Enables (1) or Disables (0) transparency effects for the Status Dialog | |
SUM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess BeepBeforeAutoLogoffEnabled: reg_dword | |||
SUM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess AutoLogoffBeepIntervalInSeconds: reg_dword | |||
SUM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess AutoLogoffBeepStartTimeInSeconds: reg_dword | |||
SUM | HKEY_LOCAL_MACHINE\SOFTWARE\HealthCast\ExactAccess AutoLogoffBeepIndex: reg_dword | 32 | May be one of the following values 0 - play sound associated with Default Beep sound in the Sound Scheme 16 - play sound associated with Critical Stop sound in the Sound Scheme 32 - play sound associated with Question sound in the Sound Scheme 48 - play sound associated with Exclamation sound in the Sound Scheme 64 - play sound associated with Asterisk sound in the Sound Scheme 4294967295 - use PC Speaker beep instead of scheme sound TipNote that the user may not have a .WAV file associated with the Sound Scheme values listed. Verify with the Sound Scheme that each of the items identified is associated with a .WAV file. These values can be found under: HKEY_CURRENT_USER \AppEvents \Schemes \Apps \<Type> \.Current -- (Default) Where <Type> is one of the following values: .Default, SystemHand, SystemQuestion, SystemExclamation, SystemAsterisk | |
SUM | HKEY_LOCAL_MACHINE\Software\HealthCast\ExactAccess\cache isCacheEnabled: reg_dword | 0 | Enables (1) or Disables (0) local credential caching |
Note
The active user list is not available in all possible configurations of workstation workflow.
Windows 7: Secure Attention Sequence (SAS) screen must be enabled for support of active user list.
Windows 10: Secure Attention Sequence (SAS) screen must be disabled for support of active user list.
Info
QAW.STATUS_BACK_COLOR and QAW.STATUS_FONT_COLOR apply a theme to the dialogs used to show the proximity card status and the user list border display.
Auto Lock - Inactivity timeouts
The autologoff.exe process now handles both locking the system, and logging the session off. Setting the Lock Time Limit setting to 2 minutes (120) and the Logoff Time Limit to 5 minutes (300) has the following effects.
After 2 minutes of inactivity, the system will lock.
After the system has been locked, and after an additional 5 minutes has elapsed (total of 7 minutes *), the system will log the current user off of ExactAccess ("XA").
Info
Previous versions of ExactAccess used the Windows Screen saver with the "secure" option to lock the workstation due to inactivity. This is no longer required, but does still function to secure the workstation. The settings above can now be used in place of configuring a screen saver.
Per-User Inactivity timeouts
It is now possible for each user session to have a customized lock and logoff timeouts independent of other users timeouts by modifying the following keys in the users/session profile registry:
HKEY_CURRENT_USER\Software\HealthCast\ExactAccess
LockTimeLimit: reg_dword = 60
LogoffTimeLimit: reg_dword = 240